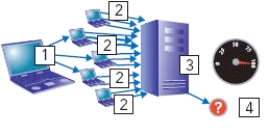
Q25: The use of nonphysical security techniques to
Q26: A _ attack occurs when a cracker
Q27: MATCHING<br>-verifying the identity of a person<br>A)spoofing<br>B)adware<br>C)steganography<br>D)spyware<br>E)port scan<br>F)port<br>G)hacker<br>H)necessity<br>I)authentication<br>J)secrecy<br>K)secret
Q28: MATCHING<br>-a component of asymmetric encryption<br>A)spoofing<br>B)adware<br>C)steganography<br>D)spyware<br>E)port scan<br>F)port<br>G)hacker<br>H)necessity<br>I)authentication<br>J)secrecy<br>K)secret key<br>L)password
Q29: You can purchase a digital signature from
Q31: A(n) _ attack involves phony email messages
Q32: A(n) _ is a small, hidden graphic
Q33: Firewalls can be used on Web _.<br>A)
Q34: The term "Web bug" is most associated
Q35: A _-bit key is considered a(n) _