Essay
Computer crime taxonomy, computer criminals and internal controls
For each independent situation below, indicate: (a) the type of computer crime based on Carter's taxonomy, (b) the type of computer criminal and (c) one internal control that would address the crime. Note to instructor: The situations in this problem are different from those in Problem 8. 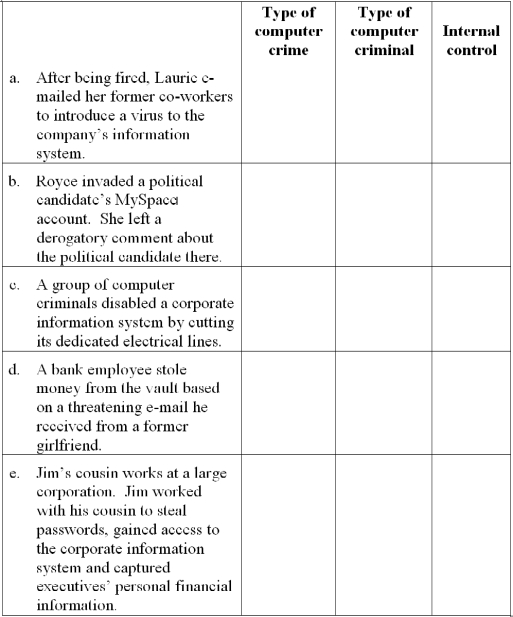
Correct Answer:

Verified
Correct Answer:
Verified
Q16: Which type of computer control is most
Q17: Errors are most likely to lead to
Q18: "Any illegal act for which knowledge of
Q19: The COBIT framework can be used to
Q20: A company installs video surveillance outside the
Q22: A hacker extracts clients' social security numbers
Q23: Information systems professionals would most likely consult
Q24: The main difference between hackers and cyber-criminals
Q25: Indicate one group from COBIT's accountability framework
Q26: On a monthly basis, internal auditors review