Deck 22: Computer Benefits and Risks
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/75
Play
Full screen (f)
Deck 22: Computer Benefits and Risks
1
In a typical LAN, the firewall is the only protection from the Internet for local devices.
False
2
Laptop computers typically consume less power than desktops.
True
3
A(n) digital certificate is issued by a certificate authority that essentially vouches for the certificate holder's identity.
True
4
A virus pattern is a section of a virus program that can be used to identify a known virus.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
5
Two networks can interconnect using a device called a(n) router .

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
6
Windows Parental Controls offer tools for establishing time limits and blocking access to specific programs.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
7
Refining is the technical method used to carry out electronic censorship by blocking Web sites, blogs, forums, or other Internet content from reaching certain audiences.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
8
A virus is the technical term for any type of intrusive program.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
9
A(n) worm is a computer program that seems to perform one function while actually doing something else.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
10
Microsoft Office provides utilities for saving files in an encrypted format.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
11
The original wireless encryption was called WPA because it was designed to provide a level of confidentiality similar to that of a wired network.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
12
The Gramm-Leach-Bliley Act (2002) established financial reporting regulations to prevent corporate fraud.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
13
Subscribing to a mailing list or RSS feed from Computer Weekly or InfoWorld can bring computer news and commentary right to your desktop.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
14
Compression utilities scramble the data in a file by using a multi-digit key.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
15
The term Intellectual property refers to intangibles, such as ideas, music, art, photos, logos, movies, and programs, that are the result of creativity and intellectual effort.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
16
Windows Defender is included with Windows 8.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
17
Malicious code can slip into your computer only through unknown Web sites.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
18
Privacy violations take place only when you distribute your personal information over the Internet.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
19
You can use a music clip or a photo on your Web site without the author's permission.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
20
Digital certificates can be attached to software, but NOT to a document or e-mail.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
21
A Trojan horse might allow a hacker to _____.
A) see the contents of your screen
B) capture your login keystrokes
C) control your Webcam
D) all of the above
A) see the contents of your screen
B) capture your login keystrokes
C) control your Webcam
D) all of the above

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
22
The process of eradicating a virus, sometimes called _____, might include deleting the virus code from files or deleting infected files.
A) erasing
B) disinfecting
C) exterminating
D) cleaning
A) erasing
B) disinfecting
C) exterminating
D) cleaning

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
23
Typically, infected attachments look like _____ files, and they infect your computer when you open them.
A) video
B) audio
C) document
D) executable
A) video
B) audio
C) document
D) executable

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
24
_____ IP addresses is the only one that can be accessed directly from the Internet.
A) A networked printer's
B) Your laptop's
C) Your PC's
D) A router's
A) A networked printer's
B) Your laptop's
C) Your PC's
D) A router's

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
25
Which of the following is the opposite of a gateway?
A) a firewall
B) an antivirus program
C) an intrusion
D) a defense wall
A) a firewall
B) an antivirus program
C) an intrusion
D) a defense wall

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
26
You should configure _____ to set Windows to display file extensions.
A) Internet Explorer
B) View Explorer
C) File Explorer
D) Extension Explorer
A) Internet Explorer
B) View Explorer
C) File Explorer
D) Extension Explorer

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
27
A key characteristic of viruses is their ability _____.
A) to see the contents of your screen
B) to perform one function while actually doing something else
C) to spread themselves from one computer to another
D) to replicate themselves on the host computer
A) to see the contents of your screen
B) to perform one function while actually doing something else
C) to spread themselves from one computer to another
D) to replicate themselves on the host computer

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
28
Which of the following files is most likely to contain a hidden virus?
A) MilesDavis.mp3
B) FinancialAid.docx.exe
C) MonthlyReport.docx
D) SlideShow.pptx
A) MilesDavis.mp3
B) FinancialAid.docx.exe
C) MonthlyReport.docx
D) SlideShow.pptx

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
29
The original wireless encryption was called _____ because it was designed to provide a level of confidentiality similar to that of a wired network.
A) WEP
B) WPA
C) WAP
D) PSK
A) WEP
B) WPA
C) WAP
D) PSK

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
30
If _____, Windows firewall should be on.
A) your computer is connected to a router
B) your computer is connected to the Internet
C) if your computer is connected to a local area network
D) your computer is not connected to the Internet
A) your computer is connected to a router
B) your computer is connected to the Internet
C) if your computer is connected to a local area network
D) your computer is not connected to the Internet

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
31
A _____ is malicious software designed to spread from computer to computer over local area networks and the Internet.
A) computer worm
B) virus
C) Trojan horse
D) none of the above
A) computer worm
B) virus
C) Trojan horse
D) none of the above

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
32
The most prevalent types of malicious code include all of the following, EXCEPT _____.
A) spam
B) viruses
C) Trojan horses
D) computer worms
A) spam
B) viruses
C) Trojan horses
D) computer worms

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
33
The data carried by Wi-Fi signals can be encrypted with all of the following, EXCEPT _____.
A) WEP
B) WPA
C) WAP
D) PSK
A) WEP
B) WPA
C) WAP
D) PSK

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
34
Some Trojan horses contain a virus or a worm, which can replicate and spread. Virus experts call this a(n) _____ threat because it combines more than one type of malicious code.
A) blended
B) combined
C) mixed-up
D) included
A) blended
B) combined
C) mixed-up
D) included

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
35
A _____ attack is designed to generate a lot of activity on a network by flooding it with useless traffic-enough traffic to overwhelm the network's processing capability and essentially bring all communications to a halt.
A) rampage
B) mass-mailing
C) denial of service
D) stampede
A) rampage
B) mass-mailing
C) denial of service
D) stampede

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
36
Which of the following antivirus software is included with Windows 8?
A) Windows Defender
B) Windows Antivirus
C) Norton
D) McAfee
A) Windows Defender
B) Windows Antivirus
C) Norton
D) McAfee

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
37
Modern antivirus software attempts to locate viruses by watching for a virus _____.
A) code
B) fingerprint
C) signature
D) pattern
A) code
B) fingerprint
C) signature
D) pattern

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
38
Which of the following is a computer program that seems to perform one function while actually doing something else?
A) spyware
B) virus
C) Trojan horse
D) computer worm
A) spyware
B) virus
C) Trojan horse
D) computer worm

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
39
Which of the following virtual ports is used to accept e-mail?
A) 80
B) 24
C) 110
D) 495
A) 80
B) 24
C) 110
D) 495

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
40
A(n) _____ worm makes use of information on an infected computer to mail itself to everyone listed in your e-mail address book.
A) post office
B) address book
C) e-mail
D) mass-mailing
A) post office
B) address book
C) e-mail
D) mass-mailing

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
41
Which of the following is a major online privacy threat today?
A) e-mail
B) Trojan horse
C) malware
D) spyware
A) e-mail
B) Trojan horse
C) malware
D) spyware

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
42
A digital certificate is issued by a(n) _____.
A) Internet service provider
B) network administrator
C) certificate authority
D) user
A) Internet service provider
B) network administrator
C) certificate authority
D) user

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
43
Circumventing copyright law and illegally copying, distributing, or modifying protected works is sometimes referred to as _____.
A) hijacking
B) piracy
C) bootlegging
D) plagiarism
A) hijacking
B) piracy
C) bootlegging
D) plagiarism

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
44
All of the following determines whether you can use material under fair use regulations, except if _____.
A) you are using the material and pretending that it is your own
B) you are using the material for educational purposes or for critical review
C) you are not using a substantial part of an entire work
D) your use does not provide a level of functionality that replaces the work, so that consumers would not need to purchase it
A) you are using the material and pretending that it is your own
B) you are using the material for educational purposes or for critical review
C) you are not using a substantial part of an entire work
D) your use does not provide a level of functionality that replaces the work, so that consumers would not need to purchase it

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
45
After using a public computer, make sure you _____.
A) sign out
B) log off
C) delete temporary Internet files
D) all of the above
A) sign out
B) log off
C) delete temporary Internet files
D) all of the above

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
46
Encryption utilities scramble the data in a file by using a _____ key.
A) password
B) multi-digit
C) 10-digit
D) compression
A) password
B) multi-digit
C) 10-digit
D) compression

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
47
Which of the following organizations works to stop illegal software distribution?
A) FBI
B) ISP
C) SIIA
D) Copyright Protection Agency
A) FBI
B) ISP
C) SIIA
D) Copyright Protection Agency

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
48
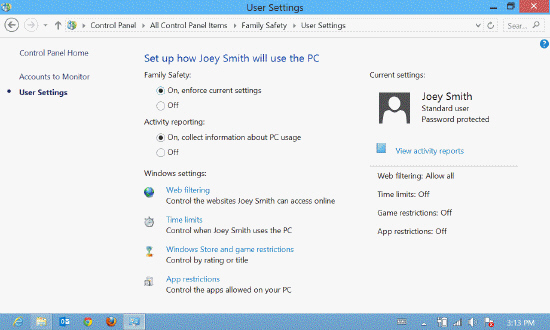 Referring to the accompanying figure, you can control all of the following, EXCEPT _____.
Referring to the accompanying figure, you can control all of the following, EXCEPT _____.A) e-mailing
B) Web filtering
C) time limits
D) Windows Store and game restrictions

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
49
Another name for a Web bug is a _____.
A) mini-GIF
B) clear GIF
C) GIF cookie
D) clear JPG
A) mini-GIF
B) clear GIF
C) GIF cookie
D) clear JPG

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
50
All of the following are steps computer owners should take to have a positive effect on the environment, EXCEPT _____.
A) recycling ink and toner cartridges
B) always making a printed copy of a document
C) configuring a computer properly to reduce power consumption
D) donating a computer to a charitable organization
A) recycling ink and toner cartridges
B) always making a printed copy of a document
C) configuring a computer properly to reduce power consumption
D) donating a computer to a charitable organization

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
51
Which one of the following laws or regulations protects ISPs from liability for defamatory statements made by customers?
A) Digital Millennium Copyright Act
B) Computer Fraud and Abuse Act
C) Communications Decency Act
D) USA PATRIOT Act
A) Digital Millennium Copyright Act
B) Computer Fraud and Abuse Act
C) Communications Decency Act
D) USA PATRIOT Act

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
52
The most popular computer magazines include all of the following, EXCEPT _____.
A) PC World
B) Computers
C) Computer Power User
D) Wired
A) PC World
B) Computers
C) Computer Power User
D) Wired

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
53
 Referring to the accompanying figure, which of the following allows a work to be used for personal purposes?
Referring to the accompanying figure, which of the following allows a work to be used for personal purposes?A) BY
B) SA
C) ND
D) NC

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
54
Some versions of Windows also include an encryption utility called _____.
A) FSE
B) WPA
C) EFS
D) WEP
A) FSE
B) WPA
C) EFS
D) WEP

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
55
Which of the following is another term for "telecommuter"?
A) teleworker
B) remote worker
C) on-line worker
D) distant worker
A) teleworker
B) remote worker
C) on-line worker
D) distant worker

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
56
To configure Internet Explorer to block third-party cookies, you should first select Internet Options from the Settings menu, then select the _____ tab.
A) Privacy
B) General
C) Security
D) Advanced
A) Privacy
B) General
C) Security
D) Advanced

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
57
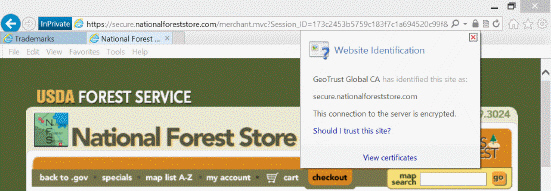 Referring to the accompanying figure, which of the following icons should you click to view a digital certificate?
Referring to the accompanying figure, which of the following icons should you click to view a digital certificate?A)

B)

C)

D)


Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
58
Which one of the following laws or regulations interprets sections of the Communications Decency Act to mean that ISPs are not responsible for malicious software transmitted over their services by hackers?
A) Digital Millennium Copyright Act (1998)
B) Gramm-Leach-Bliley Act (1999)
C) CAN-SPAM Act (2003)
D) Green v. America Online (2003)
A) Digital Millennium Copyright Act (1998)
B) Gramm-Leach-Bliley Act (1999)
C) CAN-SPAM Act (2003)
D) Green v. America Online (2003)

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
59
Which of the following refers to the use of fraudulent Web sites and e-mail links to trick people into revealing sensitive, personal, and financial information?
A) hacking
B) phishing
C) scamming
D) tricking
A) hacking
B) phishing
C) scamming
D) tricking

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
60
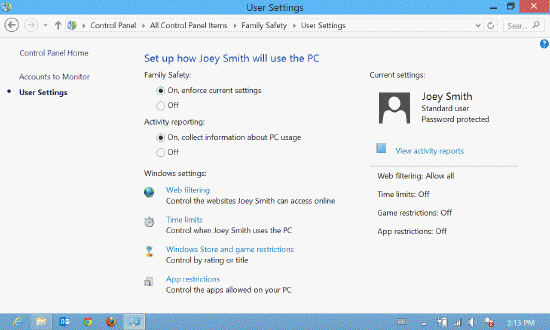 The accompanying figure illustrates the use of _____.
The accompanying figure illustrates the use of _____.A) Windows Security Controls
B) Windows Privacy Controls
C) Windows Family Safety Controls
D) Windows Parental Controls

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
61
Identity ____________________ occurs when someone obtains your personal information and uses it without your permission to commit fraud or other crimes.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
62
Never reply to ____________________ e-mails.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
63
____________________ is the use of fraudulent Web sites and e-mail links to trick people into revealing sensitive, personal, and financial information.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
64
File ____________________ software overwrites a hard disk or USB drive with random 1s and 0s to make data unrecoverable.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
65
The practice of searching the Internet for unprotected computers is called a(n) ____________________.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
66
The term ____________________ refers to any program or set of program instructions designed to surreptitiously enter a computer, disrupt its normal operations, or gather sensitive data.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
67
Case-Based Critical Thinking Questions Case 22-1 Ethan is in charge of Internet security for a small company. Employees are often asking him questions related to their identity and privacy online, as well as about some phishing schemes. Below are three of these questions. How can I protect my privacy online?
A) Promptly reply to spammers.
B) Do not use social networks like Facebook to share information about your family.
C) Use your real name when participating in chat rooms.
D) Assume that all emails are like sealed letters.
A) Promptly reply to spammers.
B) Do not use social networks like Facebook to share information about your family.
C) Use your real name when participating in chat rooms.
D) Assume that all emails are like sealed letters.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
68
____________________ software is designed to analyze the flow of traffic entering your computer from a network.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
69
On networks, ____________________ works by scrambling data as it leaves your computer so that data is in encrypted format while in transit.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
70
Case-Based Critical Thinking Questions Case 22-1 Ethan is in charge of Internet security for a small company. Employees are often asking him questions related to their identity and privacy online, as well as about some phishing schemes. Below are three of these questions. I have received an e-mail that warns about a devastating new virus, tells how to remove it, and encourages me to notify all my friends. What is this e-mail called?
A) an infection hoax
B) a virus warning
C) a virus hoax
D) a virus scam
A) an infection hoax
B) a virus warning
C) a virus hoax
D) a virus scam

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
71
____________________ software is a set of utility programs that looks for and eradicates viruses, Trojan horses, worms, and other malware.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
72
A Web ____________________ is an object, such as tiny graphic, embedded on a Web page that sends a cookie to third-party Web sites.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
73
Case-Based Critical Thinking Questions Case 22-1 Ethan is in charge of Internet security for a small company. Employees are often asking him questions related to their identity and privacy online, as well as about some phishing schemes. Below are three of these questions. Which of the following is among the most prevalent e-mail scams currently circulating?
A) funds transfers from offshore banks
B) stolen travel documents
C) Microsoft Windows logins
D) All of the above
A) funds transfers from offshore banks
B) stolen travel documents
C) Microsoft Windows logins
D) All of the above

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
74
One of the forms of malicious code is a worm. Please briefly describe a worm, a mass-mailing worm, and a denial of service attack.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
75
Explain how you can use a router to protect your computer from intrusions.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck


