Exam 22: Computer Benefits and Risks
Exam 1: Computer Hardware75 Questions
Exam 2: Peripheral Devices75 Questions
Exam 3: System and Application Software75 Questions
Exam 4: Installing Software75 Questions
Exam 5: Getting Started With Windows75 Questions
Exam 6: Working With Windows Settings and Accounts75 Questions
Exam 7: Working With Files75 Questions
Exam 8: Getting Started With Application Software75 Questions
Exam 9: Creating a Document75 Questions
Exam 10: Formatting a Document75 Questions
Exam 11: Finalizing a Document75 Questions
Exam 12: Creating a Worksheet75 Questions
Exam 13: Formatting a Worksheet75 Questions
Exam 14: Finalizing a Worksheet75 Questions
Exam 15: Creating a Presentation75 Questions
Exam 16: Finalizing a Presentation75 Questions
Exam 17: Creating a Database75 Questions
Exam 18: Finalizing a Database75 Questions
Exam 19: Networks75 Questions
Exam 20: Working With E-Mail75 Questions
Exam 21: Browsing the Web75 Questions
Exam 22: Computer Benefits and Risks75 Questions
Select questions type
A(n) digital certificate is issued by a certificate authority that essentially vouches for the certificate holder's identity.
Free
(True/False)
4.7/5  (36)
(36)
Correct Answer:
True
 The accompanying figure illustrates the use of _____.
The accompanying figure illustrates the use of _____.
Free
(Multiple Choice)
4.8/5  (28)
(28)
Correct Answer:
D
Case-Based Critical Thinking Questions Case 22-1 Ethan is in charge of Internet security for a small company. Employees are often asking him questions related to their identity and privacy online, as well as about some phishing schemes. Below are three of these questions. How can I protect my privacy online?
Free
(Multiple Choice)
4.9/5  (30)
(30)
Correct Answer:
B
All of the following determines whether you can use material under fair use regulations, except if _____.
(Multiple Choice)
4.9/5  (39)
(39)
Which of the following virtual ports is used to accept e-mail?
(Multiple Choice)
4.8/5  (36)
(36)
File ____________________ software overwrites a hard disk or USB drive with random 1s and 0s to make data unrecoverable.
(Short Answer)
4.9/5  (24)
(24)
The term ____________________ refers to any program or set of program instructions designed to surreptitiously enter a computer, disrupt its normal operations, or gather sensitive data.
(Short Answer)
4.9/5  (30)
(30)
Which one of the following laws or regulations protects ISPs from liability for defamatory statements made by customers?
(Multiple Choice)
4.9/5  (29)
(29)
Encryption utilities scramble the data in a file by using a _____ key.
(Multiple Choice)
4.8/5  (33)
(33)
Case-Based Critical Thinking Questions Case 22-1 Ethan is in charge of Internet security for a small company. Employees are often asking him questions related to their identity and privacy online, as well as about some phishing schemes. Below are three of these questions. Which of the following is among the most prevalent e-mail scams currently circulating?
(Multiple Choice)
4.8/5  (31)
(31)
The original wireless encryption was called WPA because it was designed to provide a level of confidentiality similar to that of a wired network.
(True/False)
4.8/5  (33)
(33)
Some Trojan horses contain a virus or a worm, which can replicate and spread. Virus experts call this a(n) _____ threat because it combines more than one type of malicious code.
(Multiple Choice)
4.9/5  (31)
(31)
_____ IP addresses is the only one that can be accessed directly from the Internet.
(Multiple Choice)
4.8/5  (38)
(38)
Windows Parental Controls offer tools for establishing time limits and blocking access to specific programs.
(True/False)
4.9/5  (34)
(34)
Some versions of Windows also include an encryption utility called _____.
(Multiple Choice)
4.7/5  (36)
(36)
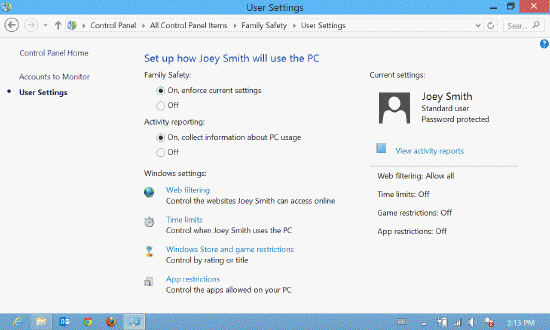
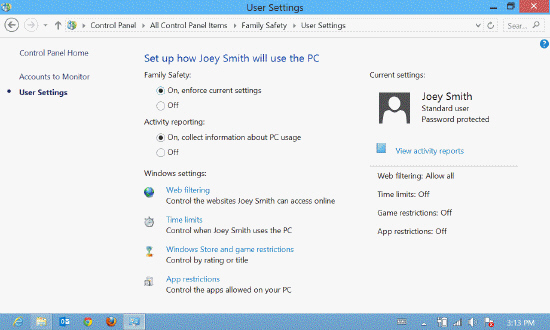 Referring to the accompanying figure, you can control all of the following, EXCEPT _____.
Referring to the accompanying figure, you can control all of the following, EXCEPT _____.
(Multiple Choice)
4.8/5  (36)
(36)
Which of the following organizations works to stop illegal software distribution?
(Multiple Choice)
5.0/5  (28)
(28)
Typically, infected attachments look like _____ files, and they infect your computer when you open them.
(Multiple Choice)
4.8/5  (40)
(40)
Showing 1 - 20 of 75
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)