Exam 5: Data Security
Exam 1: Computer and Internet Basics71 Questions
Exam 2: Computer Hardware71 Questions
Exam 3: Computer Software71 Questions
Exam 4: File Management and Digital Electronics71 Questions
Exam 5: Data Security71 Questions
Exam 6: Networks and Connecting to the Internet71 Questions
Exam 7: The Web and E-Commerce70 Questions
Exam 8: Digital Media71 Questions
Exam 9: Technology, Careers, and Job Hunting71 Questions
Select questions type
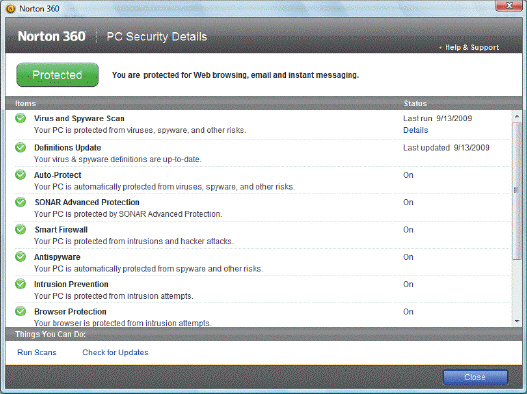 The application shown in the accompanying figure is an example of a(n) ____.
The application shown in the accompanying figure is an example of a(n) ____.
Free
(Multiple Choice)
4.8/5  (34)
(34)
Correct Answer:
D
The information that antivirus software uses to identify and remove malware is referred to as a virus ____.
Free
(Multiple Choice)
4.7/5  (31)
(31)
Correct Answer:
C
Kyle is training a new employee named Mira on how to set up measures to protect the computers and systems in their company. Kyle tells his co-worker Mira that which of the following is NOT true about cookies?
Free
(Multiple Choice)
4.9/5  (38)
(38)
Correct Answer:
B
Internet service providers use e-mail ____ techniques to verify that e-mail messages originate from the Internet domain from which they claim to have been sent.
(Multiple Choice)
4.8/5  (24)
(24)
Cyberterrorism uses viruses and worms to destroy data and disrupt computer-related operations such as power grids and telecommunication systems.
(True/False)
4.7/5  (31)
(31)
____ is the practice of intercepting signals with a Wi-Fi enabled notebook.
(Multiple Choice)
4.7/5  (42)
(42)
A(n) ____________________ strip is an appliance designed to protect electrical devices from power problems but that does not contain a battery to keep the computer running.
(Short Answer)
4.7/5  (36)
(36)
A Remote Access Trojan allows hackers to transmit files to victims' computers, search for data, run programs, and use a victim's computer as a relay station for breaking into other computers.
(True/False)
4.7/5  (42)
(42)
An email with a dire warning about a new virus is usually a virus ____________________.
(Short Answer)
4.9/5  (28)
(28)
A security suite might include detecting intrusions into your wireless network.
(True/False)
4.8/5  (37)
(37)
A(n) ____ is software or hardware designed to filter out suspicious data attempting to enter or leave a computer.
(Multiple Choice)
4.7/5  (31)
(31)
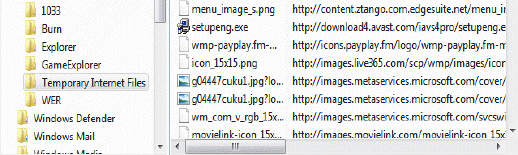 Crackers , like the kind shown in the accompanying figure, are messages containing information about the user sent from a Web server to a browser and stored on the user's hard drive.
Crackers , like the kind shown in the accompanying figure, are messages containing information about the user sent from a Web server to a browser and stored on the user's hard drive.
(True/False)
4.8/5  (38)
(38)
The objective of ____ management is to help reduce downtime, and maintain the best working conditions.
(Multiple Choice)
4.8/5  (33)
(33)
A key characteristic of a(n) ____ is the ability to lurk in a computer for days or months, quietly copying itself.
(Multiple Choice)
4.8/5  (36)
(36)
Even a brief interruption in power can force your computer to lose all data in ROM.
(True/False)
4.9/5  (41)
(41)
Port scanning software can examine more than ____ computers per minute.
(Multiple Choice)
4.8/5  (31)
(31)
A Trojan is designed to replicate itself and spread to other computers.
(True/False)
4.8/5  (35)
(35)
A ____ is a program that seems to perform one function while actually doing something else.
(Multiple Choice)
4.8/5  (37)
(37)
Showing 1 - 20 of 71
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)