Multiple Choice
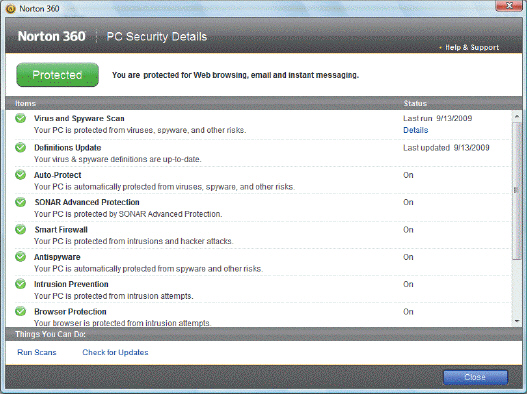 The application shown in the accompanying figure is an example of a(n) ____.
The application shown in the accompanying figure is an example of a(n) ____.
A) firewall
B) Trojan horse
C) encryption program
D) security suite
Correct Answer:

Verified
Correct Answer:
Verified
Related Questions
Q2: The information that antivirus software uses to
Q3: Kyle is training a new employee named
Q4: A(n) password usually can be entered using
Q5: Internet service providers use e-mail _ techniques
Q6: Cyberterrorism uses viruses and worms to destroy
Q7: _ is the practice of intercepting signals
Q8: A(n) _ strip is an appliance designed
Q9: A Remote Access Trojan allows hackers to
Q10: An email with a dire warning about
Q11: A security suite might include detecting intrusions