Exam 8: Security Issues, Ethics, and Emerging Technologies in Education
Exam 1: Integrating Educational Technology Into the Curriculum103 Questions
Exam 2: Communications, Networks, the Internet, and the World Wide Web103 Questions
Exam 3: Software for Educators103 Questions
Exam 4: Hardware for Educators103 Questions
Exam 5: Technology, Digital Media, and Curricul112 Questions
Exam 6: The Changing Face of Education: Teaching Online103 Questions
Exam 7: Evaluating Educational Technology and Integration Strategies103 Questions
Exam 8: Security Issues, Ethics, and Emerging Technologies in Education103 Questions
Select questions type
Possessed objects are often used in combination with a(n) ____________________ that is a numeric password that provides an additional level of security.
(Short Answer)
4.8/5  (34)
(34)
A ____ allows network users to share a single copy of the software.
(Multiple Choice)
4.8/5  (23)
(23)
An area of computer ethics frequently discussed includes ____.
(Multiple Choice)
4.8/5  (37)
(37)
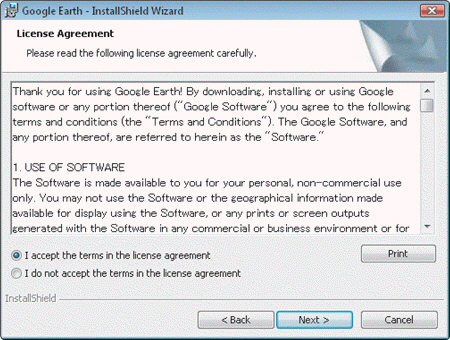 Software licenses like the one in the accompanying figure are agreements that ____.
Software licenses like the one in the accompanying figure are agreements that ____.
(Multiple Choice)
4.9/5  (35)
(35)
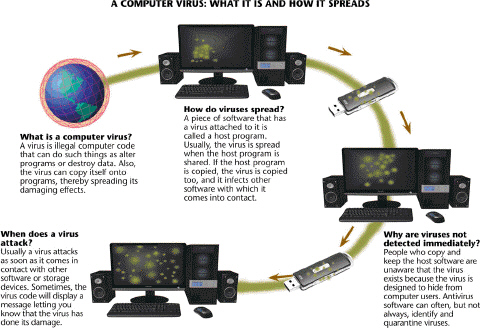 All of the following are true concerning viruses like those described in the accompanying figure EXCEPT ____.
All of the following are true concerning viruses like those described in the accompanying figure EXCEPT ____.
(Multiple Choice)
4.8/5  (34)
(34)
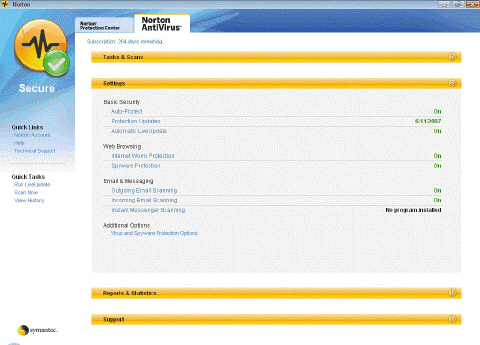 Antivirus programs like the one in the accompanying figure also are called ____.
Antivirus programs like the one in the accompanying figure also are called ____.
(Multiple Choice)
4.9/5  (31)
(31)
A(n) ____________________ gives the buyer the right to install software on multiple computers at a single site.
(Short Answer)
4.8/5  (36)
(36)
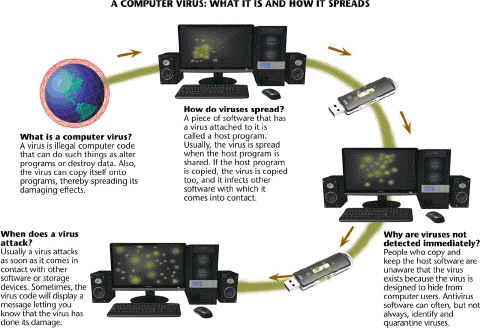 Most viruses like those described in the accompanying figure are harmless pranks that cause no permanent damage.
Most viruses like those described in the accompanying figure are harmless pranks that cause no permanent damage.
(True/False)
4.8/5  (41)
(41)
A ____ gives an entire region or state the right to install an unlimited number of educational copies of a software program.
(Multiple Choice)
4.7/5  (35)
(35)
____ computing involves reducing the use of electricity and the production of environmental waste while using a computer.
(Multiple Choice)
4.9/5  (32)
(32)
Critical Thinking Case 8-2 You believe that your information privacy has been violated. You receive a great deal of e-mail from companies trying to sell something. Which of the following is a likely cause of all the e-mail?
(Multiple Choice)
4.8/5  (30)
(30)
A worm is a malicious software program that hides within a legitimate program.
(True/False)
4.8/5  (35)
(35)
Any illegal act involving a computer generally is referred to as a computer crime.
(True/False)
4.9/5  (36)
(36)
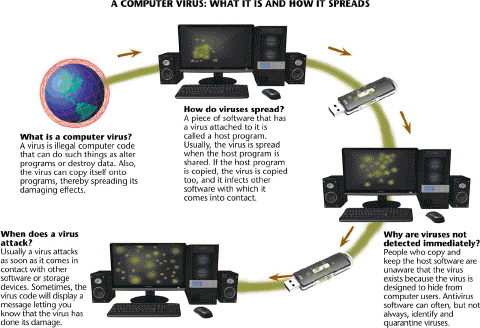 Viruses like those described in the accompanying figure commonly infect computers through e-mail attachments.
Viruses like those described in the accompanying figure commonly infect computers through e-mail attachments.
(True/False)
4.8/5  (41)
(41)
In case a file is corrupted or destroyed, a user can utilize the backup copies to ____________________, or reload, the files on a computer.
(Short Answer)
4.9/5  (33)
(33)
While an outstanding educational tool, curriculum resource pages will not significantly reduce the chances that students will view inappropriate Web sites.
(True/False)
4.8/5  (32)
(32)
____________________ is a health-related condition with symptoms including sore, tired, burning, itching, or dry eyes.
(Short Answer)
4.8/5  (32)
(32)
The daVinci virus destroys data on March 6, the date of the artist's birthday.
(True/False)
5.0/5  (31)
(31)
Showing 21 - 40 of 103
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)