Exam 8: Security Issues, Ethics, and Emerging Technologies in Education
Exam 1: Integrating Educational Technology Into the Curriculum103 Questions
Exam 2: Communications, Networks, the Internet, and the World Wide Web103 Questions
Exam 3: Software for Educators103 Questions
Exam 4: Hardware for Educators103 Questions
Exam 5: Technology, Digital Media, and Curricul112 Questions
Exam 6: The Changing Face of Education: Teaching Online103 Questions
Exam 7: Evaluating Educational Technology and Integration Strategies103 Questions
Exam 8: Security Issues, Ethics, and Emerging Technologies in Education103 Questions
Select questions type
A ____ virus replaces the program that is used to start the computer system with a modified, infected version of the startup program.
(Multiple Choice)
4.8/5  (25)
(25)
People who try to access computer systems illegally are called ____________________.
(Short Answer)
4.9/5  (35)
(35)
A backup is a duplicate of a file, program, or disk that can be used if the original is lost, damaged, or destroyed.
(True/False)
4.9/5  (35)
(35)
A community/state site license normally does not provide substantial savings over single-use licenses.
(True/False)
4.9/5  (37)
(37)
Critical Thinking Case 8-1 Your computer is not behaving normally and you need to investigate. You discover that the computer has limited resources and shuts down frequently. Which of the following viruses might your computer have?
(Multiple Choice)
4.8/5  (40)
(40)
A(n) ____________________ is defined as any event or action that could cause loss or damage to computer capabilities.
(Short Answer)
4.8/5  (31)
(31)
Software that is distributed free for a trial use period is called ____.
(Multiple Choice)
4.8/5  (41)
(41)
A(n) ____________________ is a type of logic bomb that is activated on a particular date.
(Short Answer)
4.9/5  (38)
(38)
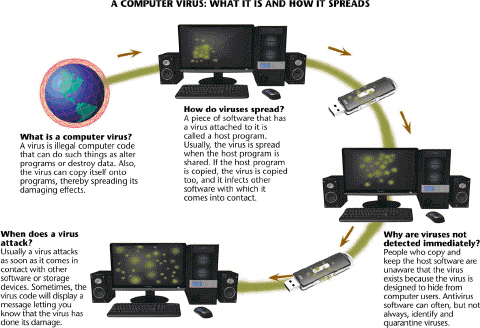 A(n) ____________________ is designed to detect, disinfect, and protect computers and networks from viruses like those in the accompanying figure.
A(n) ____________________ is designed to detect, disinfect, and protect computers and networks from viruses like those in the accompanying figure.
(Short Answer)
4.8/5  (27)
(27)
Biometrics is an applied science devoted to incorporating comfort, efficiency, and safety into the design of items in the workplace.
(True/False)
4.8/5  (34)
(34)
____ is a scam in which a perpetrator sends an official-looking e-mail that attempts to obtain personal and financial information from the recipient.
(Multiple Choice)
5.0/5  (42)
(42)
Unauthorized access is the use of a computer system or data for unapproved purposes.
(True/False)
4.9/5  (37)
(37)
A security system consisting of hardware and/or software that prevents unauthorized access to data and information on a network is called a(n) ____.
(Multiple Choice)
4.9/5  (33)
(33)
Storing backup copies at another location, called a(n) ____________________, is an additional precaution often overlooked by schools and home users.
(Short Answer)
4.9/5  (33)
(33)
Showing 81 - 100 of 103
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)