Exam 9: Operating Systems
Exam 1: Introducing Todays Technologies180 Questions
Exam 2: Connecting and Communicating Online181 Questions
Exam 3: Computers and Mobile Devices181 Questions
Exam 4: Programs and Apps181 Questions
Exam 5: Digital Security Ethics and Privacy181 Questions
Exam 6: Computing Components181 Questions
Exam 7: Input and Output181 Questions
Exam 8: Digital Storage178 Questions
Exam 9: Operating Systems181 Questions
Exam 10: Communicating Digital Content181 Questions
Exam 11: Building Solutions180 Questions
Exam 12: Working in the Enterprise181 Questions
Exam 13: Focus on Web Development66 Questions
Exam 14: Practice Test for Mindtap9 Questions
Select questions type
You want to run another operating system on your computer in addition to the one already installed. Which of the following will let you do that?
(Multiple Choice)
4.9/5  (38)
(38)
Who can establish standard user accounts that allow alterations to security settings?
(Multiple Choice)
4.9/5  (44)
(44)
Identify the letter of the choice that best matches the phrase or definition.
Correct Answer:
Premises:
Responses:
(Matching)
4.8/5  (47)
(47)
If the user name and password entered match the user name and password kept on file, an operating system grants access to the user.
(True/False)
4.9/5  (36)
(36)
List six different file and disk management tools and briefly describe their functions.
(Essay)
4.8/5  (36)
(36)
Which of the following is a set of programs containing instructions that coordinate all the activities among computer hardware resources?
(Multiple Choice)
4.9/5  (41)
(41)
Which of the following is NOT a name of an Android release?
(Multiple Choice)
4.9/5  (39)
(39)
Among file and disk management tools, a(n) ____________________ tool copies selected files or the contents of an entire storage medium to another storage location.
(Short Answer)
4.9/5  (33)
(33)
You have been developing an embedded operating system for a new product at your company, but a colleague of yours has been referring to it by another name. What is that name?
(Multiple Choice)
4.8/5  (40)
(40)
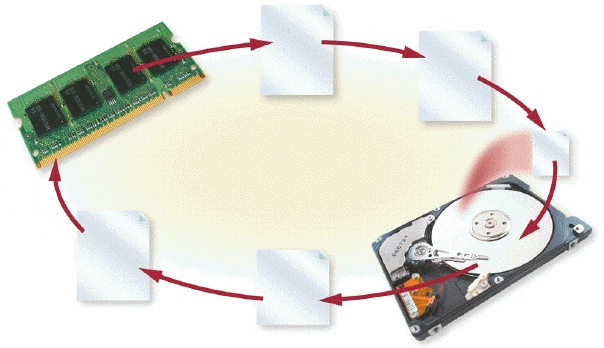 With virtual memory, which is illustrated in the accompanying figure, when an operating system spends much of its time paging, instead of executing application software, it is said to be thrashing.
With virtual memory, which is illustrated in the accompanying figure, when an operating system spends much of its time paging, instead of executing application software, it is said to be thrashing.
(True/False)
4.8/5  (36)
(36)
Which of the following is a private combination of characters associated with a user name that allows access to certain computer resources?
(Multiple Choice)
5.0/5  (41)
(41)
If a computer is running extremely slowly, the performance monitor may determine that the computer's memory is being used to its maximum.
(True/False)
4.8/5  (36)
(36)
As you interact with a program, part of it may be in physical RAM, while the rest of the program is on the hard disk as virtual memory.
(True/False)
4.8/5  (39)
(39)
A(n) ____________________ is a program that assesses and reports information about various computer resources and devices.
(Short Answer)
4.8/5  (25)
(25)
Showing 121 - 140 of 181
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)