Exam 11: Building Solutions
Exam 1: Introducing Todays Technologies180 Questions
Exam 2: Connecting and Communicating Online181 Questions
Exam 3: Computers and Mobile Devices181 Questions
Exam 4: Programs and Apps181 Questions
Exam 5: Digital Security Ethics and Privacy181 Questions
Exam 6: Computing Components181 Questions
Exam 7: Input and Output181 Questions
Exam 8: Digital Storage178 Questions
Exam 9: Operating Systems181 Questions
Exam 10: Communicating Digital Content181 Questions
Exam 11: Building Solutions180 Questions
Exam 12: Working in the Enterprise181 Questions
Exam 13: Focus on Web Development66 Questions
Exam 14: Practice Test for Mindtap9 Questions
Select questions type
In your database course, your instructor has given you a small database that has a lot of invalid data, issuing the challenge to you that you work to apply validation rules to the data and determine what checks need to be applied in order to restore integrity to the data.
A quick scan of the data in the First Name field in the database yields the numbers 3 and 7 and an asterisk. What kind of check should you run on this field?
(Multiple Choice)
4.9/5  (31)
(31)
Your database was damaged due to hardware failure. What can you use to restore it?
(Multiple Choice)
4.9/5  (38)
(38)
Which of the following is a number(s) or character(s) that is appended to or inserted into a primary key field?
(Multiple Choice)
5.0/5  (43)
(43)
Which of the following kind of checks is a validity check performed on data, which ensures users enter only alphabetic data into a field?
(Multiple Choice)
4.9/5  (42)
(42)
In what kind of recovery does the DBMS use the log to reenter changes made to a database since the last save or backup?
(Multiple Choice)
4.8/5  (35)
(35)
Like a form, a report generator is used to maintain and retrieve data.
(True/False)
4.8/5  (40)
(40)
____________________ is a common data type that consists of an email address or a web address that links to a webpage on the Internet, for example.
(Short Answer)
4.9/5  (41)
(41)
A(n) ____________________ verifies that a required field contains data.
(Short Answer)
4.9/5  (37)
(37)
In a forward recovery, the DBMS uses the log to undo any changes made to a database during a certain period, such as an hour.
(True/False)
4.9/5  (40)
(40)
Which of the following statements is NOT true about object-oriented databases (OODBs)?
(Multiple Choice)
4.9/5  (43)
(43)
The data in a database is independent of programs that access that data.
(True/False)
4.8/5  (37)
(37)
Which of the following is a window on the screen that provides areas for entering or modifying data in a database?
(Multiple Choice)
5.0/5  (38)
(38)
Which of the following statements is NOT true about multidimensional databases?
(Multiple Choice)
4.7/5  (28)
(28)
What is the term for the process of comparing data with a set of rules or values to find out if the data is correct?
(Multiple Choice)
4.9/5  (43)
(43)
Which of the following kind of checks is a validity check performed on data, which ensures users enter only numeric data into a field?
(Multiple Choice)
4.8/5  (30)
(30)
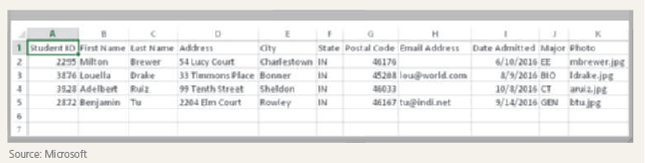 A user of a database such as that pictured in the accompanying figure refers to a file as what?
A user of a database such as that pictured in the accompanying figure refers to a file as what?
(Multiple Choice)
4.8/5  (34)
(34)
Which of the following is NOT considered a part of file maintenance?
(Multiple Choice)
4.7/5  (32)
(32)
Data integrity is important because computers and people use information to make decisions and take actions.
(True/False)
4.8/5  (42)
(42)
In the ASCII coding scheme, each byte represents a single ____________________, which can be a number, letter, blank space, punctuation mark, or other symbol.
(Short Answer)
5.0/5  (29)
(29)
Showing 21 - 40 of 180
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)