Exam 6: Understanding Internet Technologies and Security
Exam 1: Into the Internet103 Questions
Exam 2: Browsing the Web103 Questions
Exam 3: Searching the Web103 Questions
Exam 4: Communicating Online103 Questions
Exam 5: Getting More Out of the Internet103 Questions
Exam 6: Understanding Internet Technologies and Security103 Questions
Exam 7: Understanding E Business103 Questions
Select questions type
 ____ involves using devices, such as the one shown in the accompanying figure, to measure biological data to identify a user.
____ involves using devices, such as the one shown in the accompanying figure, to measure biological data to identify a user.
(Multiple Choice)
4.8/5  (46)
(46)
____ involves security audit personnel trying to hack into a network.
(Multiple Choice)
4.9/5  (35)
(35)
The DNS _________________________ consists of all of the information in the DNS databases, including the top-level domain, country code top-level domain, domain name, and IP address information.
(Short Answer)
4.9/5  (52)
(52)
Discuss wireless network security threats, including the following: LAN jacking (war driving), spoofing, and rogue WLANs.
(Essay)
4.9/5  (32)
(32)
A(n) ____ private network uses tunneling to hide encrypted data, IP addresses, and a tunneling protocol inside IP packets routed over the public network using the IP protocol.
(Multiple Choice)
4.9/5  (39)
(39)
____ networks allow voice, data, and video to be delivered simultaneously across the same network using a combination of computers and devices, telephones, and television.
(Multiple Choice)
4.9/5  (37)
(37)
A ____ topology connects each node to a central device, such as a hub or switch.
(Multiple Choice)
4.8/5  (43)
(43)
Modified Multiple Choice
Which of the following are network classifications for the assignment of IP addresses under the original classful routing system?
(Multiple Choice)
4.8/5  (37)
(37)
A(n) ____ electronically authenticates an organization's or individual's identity.
(Multiple Choice)
4.8/5  (37)
(37)
The ability of a(n) _________________________ LAN to support shared data storage, provide network maintenance tools, and promote more efficient data backups offers advantages over a peer-to-peer LAN.
(Short Answer)
4.7/5  (32)
(32)
How an organization deals with a natural or man-made disaster to ensure the organization's viability is covered by their disaster recovery plan.
(True/False)
4.8/5  (34)
(34)
Describe the process by which DNS servers resolve a domain name. Include in your response a discussion of the DNS hierarchy. Provide an example of how this works.
(Essay)
4.9/5  (36)
(36)
The ____ allows private companies to handle the registration of domain names.
(Multiple Choice)
4.8/5  (49)
(49)
The _________________________ command is used to display your computer's IP address.
(Short Answer)
4.9/5  (40)
(40)
Critical Thinking Questions Case 6-1
You are the assistant to the manager of the IT department at an auto dealership. The manager asks you to verify some Internet-related information about an auto manufacturer. You decide to use operating system utilities to verify the information.
Which operating system utility should you use to find the numeric IP address of the auto manufacturer's website when you know the domain name?
(Multiple Choice)
4.7/5  (38)
(38)
Critical Thinking Questions Case 6-1
You are the assistant to the manager of the IT department at an auto dealership. The manager asks you to verify some Internet-related information about an auto manufacturer. You decide to use operating system utilities to verify the information.
Which operating system utility should you use to verify the number of hops it takes for data to go from a computer on your network to the auto manufacturer's network?
(Multiple Choice)
4.9/5  (31)
(31)
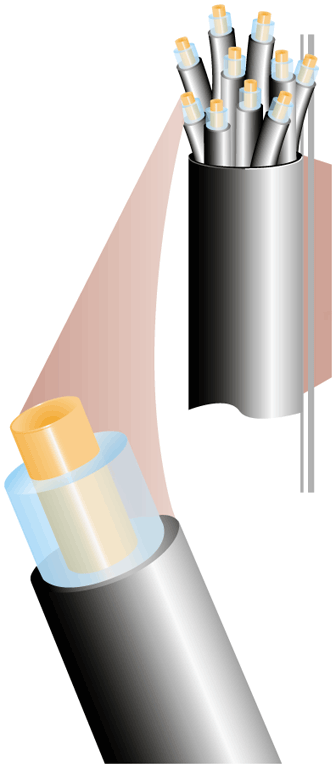 _________________________ cable, as shown in the accompanying figure, contains glass fibers surrounded by a layer of glass cladding and a protective outer jacket.
_________________________ cable, as shown in the accompanying figure, contains glass fibers surrounded by a layer of glass cladding and a protective outer jacket.
(Short Answer)
4.9/5  (43)
(43)
Most virus protection software programs perform automatic virus definition updates through downloads over the Internet.
(True/False)
4.9/5  (28)
(28)
The tracert utility can test the path to a destination Internet site and see if any problems exist with making a connection at a particular point along the route.
(True/False)
4.8/5  (32)
(32)
Showing 41 - 60 of 103
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)