Exam 6: Understanding Internet Technologies and Security
Exam 1: Into the Internet103 Questions
Exam 2: Browsing the Web103 Questions
Exam 3: Searching the Web103 Questions
Exam 4: Communicating Online103 Questions
Exam 5: Getting More Out of the Internet103 Questions
Exam 6: Understanding Internet Technologies and Security103 Questions
Exam 7: Understanding E Business103 Questions
Select questions type
A(n) token _________________________ network passes tokens, small packets of data, clockwise in a circle from node to node.
(Short Answer)
4.9/5  (27)
(27)
A(n) ____ is the combination of organizations or individuals sending and receiving encrypted data, their public and private keys, and the CAs that issue the keys and digital certificates.
(Multiple Choice)
4.9/5  (39)
(39)
Personal VPNs exist wherein mobile or wireless users can establish a private, secure network connection.
(True/False)
4.7/5  (37)
(37)
An example of a short-range RF technology that sends and receives wireless transmissions between devices such as computers, smartphones, tablets, and headsets is ____.
(Multiple Choice)
4.8/5  (38)
(38)
Modified Multiple Choice
Internet telephony is also called _____.
(Multiple Choice)
4.8/5  (33)
(33)
A security audit may result in a revision of security policies and procedures, improved employee training, and making necessary updates to the network's hardware and software.
(True/False)
4.9/5  (42)
(42)
A(n) ____ meeting allows collaboration between participants, such as a group of employees, over a network.
(Multiple Choice)
4.9/5  (45)
(45)
A transceiver is a single component that both sends and receives transmissions.
(True/False)
4.9/5  (36)
(36)
The primary tools used to provide transaction authentication, integrity, nonrepudiation, and confidentiality are encryption and dynamic routing.
(True/False)
4.7/5  (42)
(42)
A token ring is a program that appears to do something useful or fun, but actually does something destructive, including destroying files, creating a way for a hacker to breach network security, and stealing passwords.
(True/False)
4.8/5  (44)
(44)
____ often exploit well-known security vulnerabilities in popular software to spread destructive programs such as viruses, worms, and Trojan horses.
(Multiple Choice)
4.8/5  (36)
(36)
When an organization wants to use encryption, it requests a set of associated public and private keys from a ____.
(Multiple Choice)
4.9/5  (39)
(39)
A credit card is a plastic card containing memory chips that can store special access codes or biometric information.
______________________
(True/False)
4.7/5  (33)
(33)
Multiple groups of computers and devices that share a common function are called _________________________.
(Short Answer)
4.8/5  (41)
(41)
Twisted-pair cable, which contains glass fibers surrounded by a layer of glass cladding and a protective outer jacket, is used to carry voice, video, and data transmissions over very long distances.
(True/False)
4.8/5  (35)
(35)
A(n) _________________________ is an internal expansion card that enables a computer or other device to access a network.
(Short Answer)
4.8/5  (33)
(33)
Data restore procedures should be tested periodically to ensure that the backed up data is correct and complete, and that the storage media or cloud-based storage service works properly.
(True/False)
4.9/5  (38)
(38)
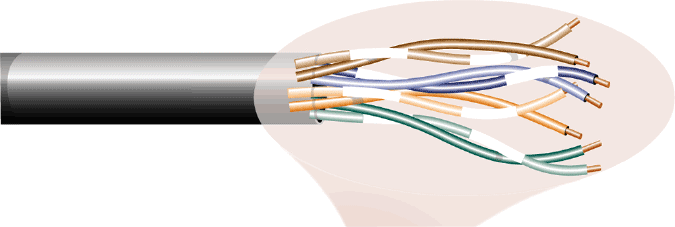 As shown in the accompanying figure, ____ cable is commonly used in LAN transmissions because it is easier to install than other types of cable and can handle the faster transmissions speeds required by modern networks.
As shown in the accompanying figure, ____ cable is commonly used in LAN transmissions because it is easier to install than other types of cable and can handle the faster transmissions speeds required by modern networks.
(Multiple Choice)
4.8/5  (41)
(41)
The _________________________ command is used to find the numeric IP address that corresponds to a domain name and vice versa.
(Short Answer)
4.9/5  (36)
(36)
Showing 81 - 100 of 103
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)