Exam 4: Account-Based Security
Exam 1: Operating Systems Security: Keeping Computers and Networks Secure86 Questions
Exam 2: Viruses, Worms, and Malicious Software86 Questions
Exam 3: Security Through Authentication and Encryption86 Questions
Exam 4: Account-Based Security86 Questions
Exam 6: Firewalls and Border Security86 Questions
Exam 7: Physical and Network Topology Security86 Questions
Exam 8: Wireless Security86 Questions
Exam 9: Web, Remote Access, and VPN Security86 Questions
Exam 10: E-Mail Security86 Questions
Exam 11: Security Through Disaster Recovery86 Questions
Exam 12: Security Through Monitoring and Auditing86 Questions
Select questions type
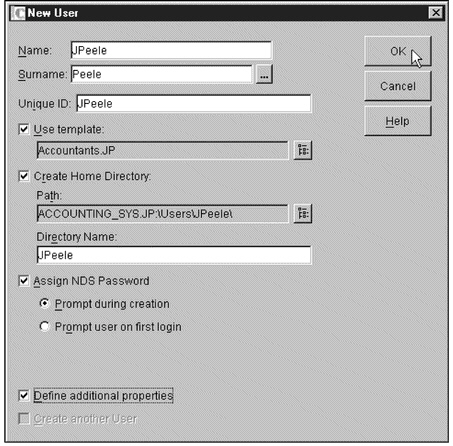 Which operating system uses the dialog in the figure above to create accounts?
Which operating system uses the dialog in the figure above to create accounts?
Free
(Multiple Choice)
4.8/5  (37)
(37)
Correct Answer:
D
An effective defense against attackers is the use of long passwords.
Free
(True/False)
4.9/5  (35)
(35)
Correct Answer:
False
Which functional area in the Windows Server 2003 is used to require digitally signed communications with the server and to control what happens when a user's session is idle or when the logon hours expire?
Free
(Multiple Choice)
4.8/5  (30)
(30)
Correct Answer:
B
In Red Hat Linux, are the group names that a user belongs to included in the /etc/passwd file?
(True/False)
4.9/5  (31)
(31)
What three account lockout options are available in Windows 2000 Server and Windows Server 2003?
(Essay)
5.0/5  (33)
(33)
If the payroll supervisor of a company decides to leave the company, should the administrator disable his or her account?
(True/False)
4.7/5  (33)
(33)
Windows 2000/XP Professional is designed to support a maximum of 2 simultaneous _________________________ users using a dial-up connection.
(Short Answer)
4.8/5  (32)
(32)
What are the six specific password security options that can be in Windows 2000 Server and Windows Server 2003?
(Essay)
4.9/5  (36)
(36)
The advantage of having accounts based on the position or function is that, for the sake of security, it is easier to know who is logged on to a server.
(True/False)
4.8/5  (33)
(33)
____________________ accounts not only provides orderly access to server and network resources, it also enables server administrators to maintain security by monitoring which users are accessing the server and what resources they are using.
(Short Answer)
4.9/5  (33)
(33)
In Red Hat Linux, is every account a member of a least one group?
(True/False)
4.8/5  (29)
(29)
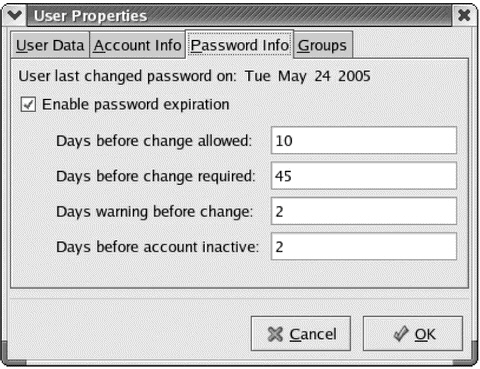 Which operating system uses the dialog in the figure above to configure password settings?
Which operating system uses the dialog in the figure above to configure password settings?
(Multiple Choice)
4.8/5  (34)
(34)
What type of accounts are created when Active Directory is not installed on Windows Server 2003?
(Multiple Choice)
4.8/5  (33)
(33)
If Active Directory is installed and you are working on a DC, Windows 2000 Server and Windows Server 2003 will not allow you to use the Local Users and Groups tool.
(True/False)
4.9/5  (38)
(38)
Windows 2000 group policy has evolved from the Windows NT Server 4.0 concept of ____________________.
(Short Answer)
4.9/5  (26)
(26)
Which account properties tab enables you to enter or modify personal information about the account holder , including the first name and last name?
(Multiple Choice)
4.9/5  (26)
(26)
The most efficient way to assign user rights is to assign them to ____________________ instead of to individual user accounts.
(Short Answer)
4.8/5  (36)
(36)
Is the option "User must change password at next logon" necessary for accounts used by the server administrator in WIndows 2003?
(True/False)
4.9/5  (36)
(36)
Administrative templates are preconfigured group policies for which of the following?
(Multiple Choice)
4.9/5  (34)
(34)
Showing 1 - 20 of 86
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)