Exam 5: CIW Web Foundations Associate
Exam 1: CIW v5 Site Designer83 Questions
Exam 2: CIW E-Commerce Designer86 Questions
Exam 3: CIW v5 Database Design Specialist75 Questions
Exam 4: CIW v5 Security Essentials48 Questions
Exam 5: CIW Web Foundations Associate138 Questions
Exam 6: CIW Internet Business Associate14 Questions
Exam 7: CIW Site Development Associate15 Questions
Exam 8: CIW Network Technology Associate8 Questions
Exam 9: CIW User Interface Designer49 Questions
Exam 10: CIW JavaScript Specialist30 Questions
Select questions type
Proprietary information for your company's online business was released to a competitor. Which of the following preventative measures should your company take to ensure that its proprietary information is protected in the future?
(Multiple Choice)
4.8/5  (38)
(38)
When using cloud-based services to host company data, a company's disaster recovery plan should include strategies for:
(Multiple Choice)
4.8/5  (43)
(43)
You are expecting a very important file from a co-worker in a remote office to be sent to you through e-mail. You finally call the co-worker and tell him that you have not received the file. He informs you that he sent the file yesterday, but will send it again immediately. After some time, you still have not received his e-mail message. You contact the Technical Support department and ask them for help. After some investigation, Technical Support finds the e-mail from your coworker with an attachment named salesnumbers.exe in the spam folder of your e-mail client. What is the most likely reason that the e-mail message was filtered out?
(Multiple Choice)
4.8/5  (39)
(39)
Gabby suspects that an attacker has gained control of her system. Which of the following is the most appropriate action for her to take?
(Multiple Choice)
4.9/5  (31)
(31)
Marion is formatting a simple Web page. She has been asked to create headings before the first and third paragraphs. To accomplish this most efficiently, which type of HTML elements should Marion use?
(Multiple Choice)
4.8/5  (33)
(33)
What does the following represent? 2E22: 4F00: 000E: 00D0:A267:97FF:FE6E:FE34
(Multiple Choice)
4.8/5  (26)
(26)
You are creating a style sheet to format your Web pages. For the page background color, you enter the hexadecimal code FF0000. What color will the page background be when you apply this style?
(Multiple Choice)
4.8/5  (31)
(31)
Katie developed her corporation's intra net site using proprietary HTML language extensions based on the company's current browser. The company has recently updated its systems to include the use of a new browser. Now the intra net site that Katie developed no longer renders its content consistently. What should Katie do to ensure that this site's content renders consistently regardless of the browser used?
(Multiple Choice)
4.9/5  (36)
(36)
Which organization is responsible for managing domain names so that each one is unique, and (once registered) cannot be used by an unauthorized individual or organization?
(Multiple Choice)
4.8/5  (38)
(38)
You are using an e-mail client that you are unfamiliar with. You need to send an e-mail with an attachment but you do not see a feature labeled "attachment" anywhere on the client. What icon should you look for that is commonly used to invoke the e-mail attachment option?
(Multiple Choice)
4.8/5  (44)
(44)
Web developers typically include comments in their code for which reason?
(Multiple Choice)
4.8/5  (30)
(30)
Which Web-based validation tool is used to validate HTML documents?
(Multiple Choice)
4.8/5  (39)
(39)
To restore a backup file on a Windows-based computer, you:
(Multiple Choice)
4.7/5  (36)
(36)
Which of the following is a security threat commonly associated with cloud-based services?
(Multiple Choice)
4.9/5  (42)
(42)
Which of the following strategies will help protect your computer against virus attacks?
(Multiple Choice)
4.8/5  (40)
(40)
To define a circle-shaped hot-spot for an image map, which of the following code fragments would you use? 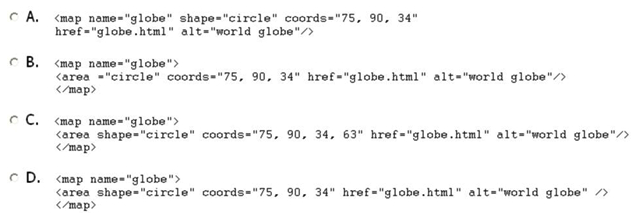
(Multiple Choice)
4.9/5  (35)
(35)
Irena is reviewing several promotional product videos from her company's marketing department before they are published on the company's Web site. The videos are in RealMedia format, but they do not open in Irena's Windows Media Player. What should Irena do in order to view the videos?
(Multiple Choice)
4.9/5  (37)
(37)
Which of the following is generally a component of a BYOD policy?
(Multiple Choice)
4.8/5  (40)
(40)
Disaster recovery planning is considered a best practice for all organizations. It is even more important when cloud-computing services are used. Which of the following should be included as part of a disaster recovery plan for companies that use cloud-based services?
(Multiple Choice)
4.9/5  (32)
(32)
Evonka is listening to music from an online music provider (such as Pandora or Jango). She builds a list of music preferences, including favorite songs. The music service then suggests additional songs she might enjoy. The music provider is an example of a cloud-computing application that uses a technology for collaborative filtering, which helps define the list of songs available to listeners. Which term describes this technology?
(Multiple Choice)
4.9/5  (32)
(32)
Showing 101 - 120 of 138
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)