Exam 2: Administration of Symantec Email Security.cloud (v1)
Exam 1: Administration of Symantec Endpoint Protection 14 (Broadcom)165 Questions
Exam 2: Administration of Symantec Email Security.cloud (v1)113 Questions
Exam 3: Administration of Symantec Data Loss Prevention 12 (Broadcom)98 Questions
Exam 4: Administration of Symantec ProxySG 6.7138 Questions
Exam 5: Symantec Messaging Gateway 10.5 Technical Assessment (Broadcom)409 Questions
Select questions type
What steps should an administrator take to utilize Symantec Endpoint Protection in a non-persistent virtual desktop infrastructure?
(Multiple Choice)
4.8/5  (39)
(39)
A Symantec Endpoint Protection (SEP) administrator creates a firewall policy to block FTP traffic and assigns the policy to all of the SEP clients. The network monitoring team informs the administrator that a client system is making an FTP connection to a server. While investigating the problem from the SEP client GUI, the administrator notices that there are zero entries pertaining to FTP traffic in the SET Traffic log or Packet log. While viewing the Network Activity dialog, there is zero inbound/outbound traffic for the FTP process. What is the most likely reason?
(Multiple Choice)
4.8/5  (34)
(34)
Which task should an administrator perform to troubleshoot operation of the Symantec Endpoint Protection embedded database?
(Multiple Choice)
4.8/5  (35)
(35)
A Symantec Endpoint Protection (SEP) administrator performed a disaster recovery without a database backup. In which file should the SEP administrator add "scm.agent.groupcreation=true" to enable the automatic creation of client groups?
(Multiple Choice)
4.7/5  (33)
(33)
Why is Notepad unable to save the changes to the file in the image below? 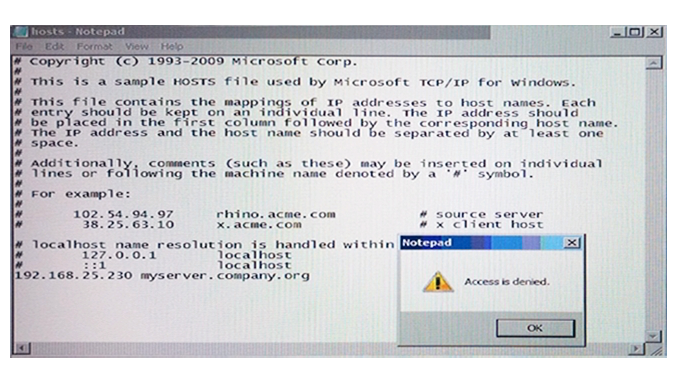
(Multiple Choice)
4.8/5  (44)
(44)
An organization needs to add a collection of DNS host names to permit in the firewall policy. How should the SEP Administrator add these DNS host names as a single rule in the firewall policy?
(Multiple Choice)
4.9/5  (36)
(36)
Which policy should an administrator modify to enable Virtual Image Exception (VIE) functionality?
(Multiple Choice)
4.9/5  (47)
(47)
An administrator is troubleshooting a Symantec Endpoint Protection (SEP) replication. Which component log should the administrator check to determine whether the communication between the two sites is working correctly?
(Multiple Choice)
4.9/5  (40)
(40)
An administrator selects the Backup files before attempting to repair the Remediations option in the Auto-Protect policies. Which two actions occur when a virus is detected? (Select two.)
(Multiple Choice)
4.9/5  (28)
(28)
A Symantec Endpoint Protection administrator must block traffic from an attacking computer for a specific time period. Where should the administrator adjust the time to block the attacking computer?
(Multiple Choice)
5.0/5  (34)
(34)
What type of exceptions can an administrator create from the Symantec Endpoint Protection Manager for a Mac client?
(Multiple Choice)
4.9/5  (34)
(34)
An organization has four locations setup in their Symantec Endpoint Protection Environment to match the physical sites they have - NAM, LATAM, EMEA, and APAC. When users travel from site to site, they would like to control which SEPM a client connects to based on the client's proximity to the nearest SEPM server. The location is triggered by IP range assigned by the DHCP of that site. How can the organization utilize Locations to control which SEPM or set of SEPMs the clients connect to?
(Multiple Choice)
4.9/5  (32)
(32)
An administrator is recovering from a Symantec Endpoint Manager (SEPM) site failure. Which file should the administrator use during an install of SEPM to recover the lost environment according to Symantec Disaster Recovery Best Practice documentation?
(Multiple Choice)
4.9/5  (34)
(34)
Which Symantec Endpoint Protection defense mechanism provides protection against threats that propagate from system to system through the use of autorun.inf files?
(Multiple Choice)
4.9/5  (43)
(43)
How should an administrator set up an alert to be notified when manual remediation is needed on an endpoint?
(Multiple Choice)
4.8/5  (39)
(39)
Which two settings does an administrator enable to use the Risk Tracer Feature in the Virus and Spyware Protection policy? (Select two.)
(Multiple Choice)
4.8/5  (46)
(46)
Which protection technology can detect botnet command and control traffic generated on the Symantec Endpoint Protection client machine?
(Multiple Choice)
5.0/5  (32)
(32)
Which two criteria should an administrator use when defining Location Awareness for the Symantec Endpoint Protection (SEP) client? (Select two.)
(Multiple Choice)
4.9/5  (48)
(48)
A company plans to install six Symantec Endpoint Protection Managers (SEPMs) spread evenly across two sites. The administrator needs to direct replication activity to SEPM3 server in Site 1 and SEPM4 in Site 2. Which two actions should the administrator take to direct replication activity to SEPM3 and SEPM4? (Select two.)
(Multiple Choice)
4.9/5  (31)
(31)
Showing 61 - 80 of 113
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)