Exam 3: Administration of Symantec Data Loss Prevention 12 (Broadcom)
Exam 1: Administration of Symantec Endpoint Protection 14 (Broadcom)165 Questions
Exam 2: Administration of Symantec Email Security.cloud (v1)113 Questions
Exam 3: Administration of Symantec Data Loss Prevention 12 (Broadcom)98 Questions
Exam 4: Administration of Symantec ProxySG 6.7138 Questions
Exam 5: Symantec Messaging Gateway 10.5 Technical Assessment (Broadcom)409 Questions
Select questions type
What does each proxy service define? (Choose two.)
Free
(Multiple Choice)
4.8/5  (34)
(34)
Correct Answer:
B,C
Why is Kerberos performance better than NTLM?
Free
(Multiple Choice)
4.8/5  (39)
(39)
Correct Answer:
B
What module should an administrator utilize to view all the activities in cloud applications and conduct analysis?
Free
(Multiple Choice)
4.8/5  (38)
(38)
Correct Answer:
A
What should an administrator do with a cloud application that does NOT meet the compliance requirements, but has mitigating controls available?
(Multiple Choice)
4.8/5  (47)
(47)
Where in the Management Console would you look to find all sessions that are being intercepted by the services framework of the ProxySG?
(Multiple Choice)
4.8/5  (49)
(49)
Which CloudSOC module is similar to a Data Loss Prevention (DLP) system?
(Multiple Choice)
4.8/5  (37)
(37)
Refer to the exhibit. An administrator found several incidents like this in the Investigate module. What type of detector should an administrator modify to reduce the frequency of this type of incident? 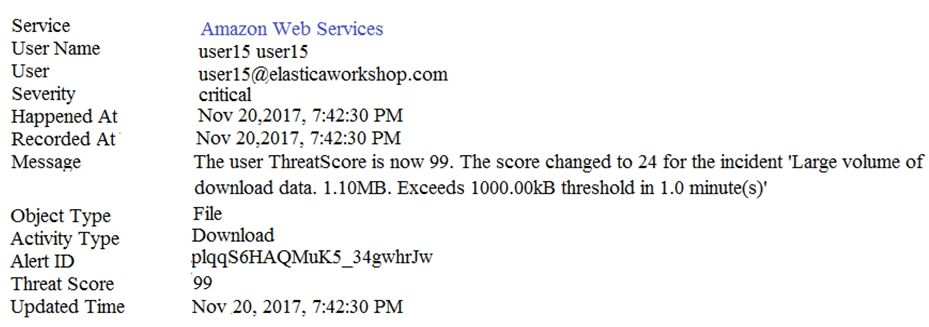
(Multiple Choice)
4.8/5  (40)
(40)
What are three (3) main risks that CloudSOC solves in cloud applications?
(Multiple Choice)
4.9/5  (44)
(44)
Which type of a policy can perform a user log out from Single Sign On?
(Multiple Choice)
4.8/5  (47)
(47)
Which CloudSOC module is similar to an Intrusion Protection System (IPS)/Intrusion Detection System (IDS)?
(Multiple Choice)
4.9/5  (37)
(37)
Which of the following are always included in both the request and response headers?
(Multiple Choice)
4.9/5  (32)
(32)
What CloudSOC module should an administrator use to prevent the accidental and intentional exposure of information within cloud applications?
(Multiple Choice)
4.9/5  (36)
(36)
Of the methods that the ProxySG uses to detect file type, which one is usually the most accurate?
(Multiple Choice)
4.8/5  (43)
(43)
Refer to the exhibit. What modules are used by the use case "Identify and determine business risk of cloud applications being used within the organization"? 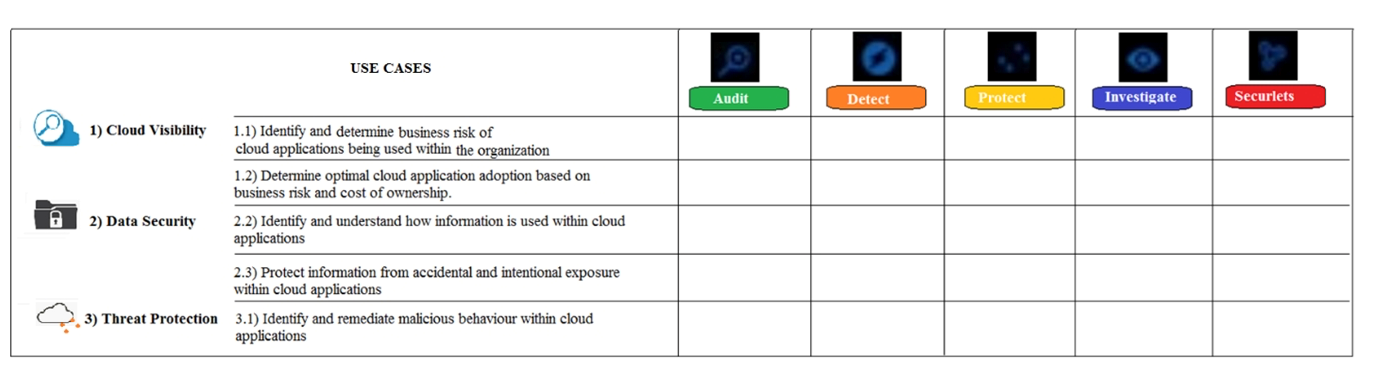
(Multiple Choice)
4.8/5  (30)
(30)
What policy should an administrator utilize to prevent users from downloading files from Box.com when they are outside the corporate IP range?
(Multiple Choice)
4.9/5  (42)
(42)
Showing 1 - 20 of 98
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)