Exam 5: Local Area Networks
Exam 1: Computers and Digital Basics147 Questions
Exam 2: Computer Hardware150 Questions
Exam 3: Software149 Questions
Exam 4: Operating Systems and File Management150 Questions
Exam 5: Local Area Networks150 Questions
Exam 6: The Internet149 Questions
Exam 7: The Web and E-mail150 Questions
Exam 8: Digital Media150 Questions
Exam 9: The Computer Industry: History,Careers,and Ethics150 Questions
Exam 10: Information Systems Analysis and Design150 Questions
Exam 11: Databases150 Questions
Exam 12: Computer Programming150 Questions
Select questions type
The process of converting ciphertext into plaintext is called encryption._________________________
(True/False)
4.7/5  (39)
(39)
Most routers ship with a(n)____ predefined by the manufacturer.
(Multiple Choice)
5.0/5  (30)
(30)
A ____ is a network device that intelligently facilitates communication among multiple devices on a network.
(Multiple Choice)
4.7/5  (37)
(37)
Ethernet is a wired technology that is defined by ____ standards.
(Multiple Choice)
4.8/5  (32)
(32)
____________________ encryption is loosely defined as "very difficult to break."
(Short Answer)
5.0/5  (33)
(33)
You have just secured a new job with a new firm that is very security conscious. You’ve been instructed to learn as much as possible about encryption to ensure the confidentiality of customer transactions as well as electronic communications about new research and development projects.
-After researching this topic,you find that encryption can be used in ____.
(Multiple Choice)
4.9/5  (36)
(36)
Dial-up Internet access is an example of a(n)____ communications system.
(Multiple Choice)
4.9/5  (29)
(29)
A message that has not been encrypted is referred to as ____.
(Multiple Choice)
4.8/5  (35)
(35)
If you connect to a network and do not get a list of other devices,check your computer's network ____ setting.
(Multiple Choice)
4.8/5  (38)
(38)
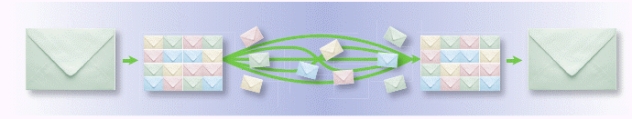 -A more efficient alternative to packet switching is shown in the accompanying figure._________________________
-A more efficient alternative to packet switching is shown in the accompanying figure._________________________
(True/False)
4.8/5  (41)
(41)
A ____ is a term sometimes used to refer to the interconnection of personal digital devices or consumer electronics within a range of about 30 feet and without the use of wires or cables.
(Multiple Choice)
4.9/5  (38)
(38)
MATCHING
Identify the letter of the choice that best matches the phrase or definition.
-A word,number,or phrase that must be known to decrypt or encrypt a message
(Multiple Choice)
4.7/5  (31)
(31)
High-bandwidth communications systems are sometimes referred to as ____.
(Multiple Choice)
4.7/5  (40)
(40)
____ software may be used by personal computer users when they want to encrypt e-mail or other documents.
(Multiple Choice)
4.9/5  (40)
(40)
In ____ mode two Bluetooth devices can find each other and exchange passkeys.
(Multiple Choice)
4.9/5  (42)
(42)
A ____ server is a computer whose primary purpose is to be a repository for files that can be accessed by network workstations.
(Multiple Choice)
4.8/5  (31)
(31)
Devices with one or more antennas use ____ technology to boost signals and spread them more evenly over the signal range.
(Multiple Choice)
4.9/5  (32)
(32)
Thomas is a network expert, having mastered the finer points of network structure, topology, and geographical scope. He has built many different types of networks at home, school, and work. He is now designing a home network for his friend.
-Thomas's friend has asked that the network be configured such that,if he has photos on his tablet computer and wants to transfer them to his desktop computer,he can do so easily.What capability is Thomas's friend looking for?
(Multiple Choice)
4.9/5  (38)
(38)
Showing 121 - 140 of 150
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)