Exam 7: The Web and E-mail
Exam 1: Computers and Digital Basics147 Questions
Exam 2: Computer Hardware150 Questions
Exam 3: Software149 Questions
Exam 4: Operating Systems and File Management150 Questions
Exam 5: Local Area Networks150 Questions
Exam 6: The Internet149 Questions
Exam 7: The Web and E-mail150 Questions
Exam 8: Digital Media150 Questions
Exam 9: The Computer Industry: History,Careers,and Ethics150 Questions
Exam 10: Information Systems Analysis and Design150 Questions
Exam 11: Databases150 Questions
Exam 12: Computer Programming150 Questions
Select questions type
To avoid becoming a spam victim,you should ____.
Free
(Multiple Choice)
4.8/5  (40)
(40)
Correct Answer:
D
HTML ____ are used to display a question and a box into which you can enter an answer.
Free
(Multiple Choice)
5.0/5  (39)
(39)
Correct Answer:
D
When you use a search engine,it stores all of the following information about your query EXCEPT ____.
Free
(Multiple Choice)
4.9/5  (32)
(32)
Correct Answer:
A
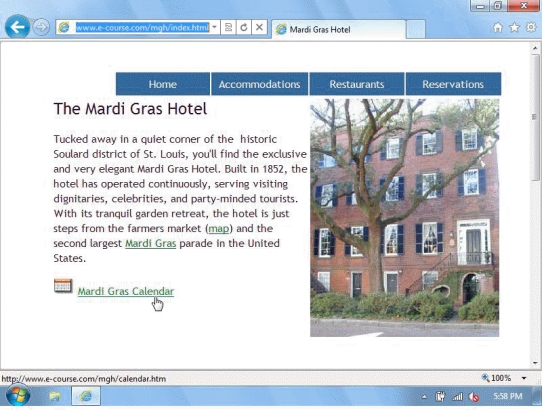 -The hand icon shown in the accompanying figure is pointing to a ____.
-The hand icon shown in the accompanying figure is pointing to a ____.
(Multiple Choice)
4.8/5  (47)
(47)
 -In the URL found in the accompanying figure,showbiz is a ____.
-In the URL found in the accompanying figure,showbiz is a ____.
(Multiple Choice)
4.8/5  (34)
(34)
You just sent an e-mail message to your co-worker that includes the following message body:
MARY-
CAN YOU PLEASE TELL ME WHEN YOU WILL HAVE THE REPORTS COMPLETED?
Why might your coworker be offended by the message?
(Multiple Choice)
4.9/5  (48)
(48)
In addition to using search engines,you can also find Web-based information using a(n)____ engine that searches a series of other search engines and compiles the search results.
(Multiple Choice)
4.9/5  (35)
(35)
An e-mail scam designed to persuade you into revealing confidential information by replying to an e-mail is called ____.
(Multiple Choice)
4.9/5  (36)
(36)
Server-side scripts can be written using any of the following EXCEPT ____.
(Multiple Choice)
4.9/5  (40)
(40)
____ e-commerce occurs when businesses sell to governments.
(Multiple Choice)
4.7/5  (34)
(34)
MATCHING
Identify the letter of the choice that best matches the phrase or definition.
-Represents one end of a connection
(Multiple Choice)
4.9/5  (43)
(43)
____________________ is an exploit that redirects users to fake sites by poisoning a domain name server with a false IP address.
(Short Answer)
4.8/5  (32)
(32)
A Web ____,automated to methodically visit Web sites,can be programmed to perform various activities as it visits those sites.
(Multiple Choice)
4.7/5  (40)
(40)
____ consists of a series of instructions that is embedded directly into an HTML document that instruct the browser to carry out specific actions or to respond to specific user actions.
(Multiple Choice)
5.0/5  (29)
(29)
Melissa has decided to obtain an e-mail account. Although she plans to use the e-mail account to communicate with her many friends, her main purpose in establishing it is to aid in the search for a job. She has a list of e-mail addresses for a group of potential employers. Melissa intends to e-mail her resume, along with a general message, to each of them. She will use the same message for all recipients.
-Melissa is planning to travel a great deal in the coming weeks.She will not be taking her computer with her,but knows that the hotels she will be staying at have business centers with Internet-enabled computers.She plans to access her e-mail account every day so that she can quickly respond should she be contacted by a prospective employer.Which one of the following account types should she use?
(Multiple Choice)
4.7/5  (35)
(35)
 -In the URL found in the accompanying figure,http is the ____.
-In the URL found in the accompanying figure,http is the ____.
(Multiple Choice)
4.8/5  (37)
(37)
____________________ is a type of security software designed to identify and neutralize Web bugs,ad-serving cookies,and other spyware.
(Short Answer)
4.9/5  (37)
(37)
When working with ____ mail,make sure your antivirus software is checking incoming messages.
(Multiple Choice)
4.9/5  (31)
(31)
Showing 1 - 20 of 150
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)