Exam 7: The Web and E-mail
Exam 1: Computers and Digital Basics147 Questions
Exam 2: Computer Hardware150 Questions
Exam 3: Software149 Questions
Exam 4: Operating Systems and File Management150 Questions
Exam 5: Local Area Networks150 Questions
Exam 6: The Internet149 Questions
Exam 7: The Web and E-mail150 Questions
Exam 8: Digital Media150 Questions
Exam 9: The Computer Industry: History,Careers,and Ethics150 Questions
Exam 10: Information Systems Analysis and Design150 Questions
Exam 11: Databases150 Questions
Exam 12: Computer Programming150 Questions
Select questions type
____ may pose a threat to your computer's security and/or your privacy.
(Multiple Choice)
4.8/5  (42)
(42)
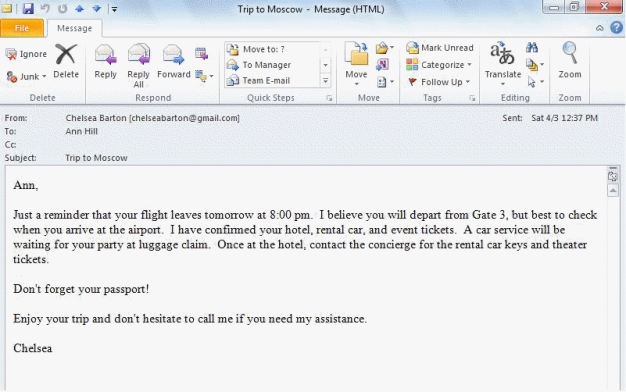 -If Chelsea Barton were sending a Word document along with the message in the accompanying figure,that document would be considered an e-mail ____________________.
-If Chelsea Barton were sending a Word document along with the message in the accompanying figure,that document would be considered an e-mail ____________________.
(Short Answer)
4.9/5  (29)
(29)
Individuals who prefer not to leave a trail of their Internet activities surf through a(n)____________________ proxy service,which uses an intermediary server to relay Web page requests after masking the originating IP address.
(Short Answer)
4.8/5  (36)
(36)
Incoming mail can be stored on a(n)____ server until it is downloaded to the inbox on your hard disk.
(Multiple Choice)
4.9/5  (36)
(36)
The ____________________ is a collection of files that can be linked and accessed using HTTP.
(Short Answer)
4.9/5  (29)
(29)
Banner and pop-up ads earn revenue for hosting merchants based on the ____________________,which is the number of times that site visitors click the ad to connect to the advertiser's site.
(Short Answer)
4.8/5  (40)
(40)
For HTTP,____ usually are associated with port 80 on the client and server.
(Multiple Choice)
4.9/5  (39)
(39)
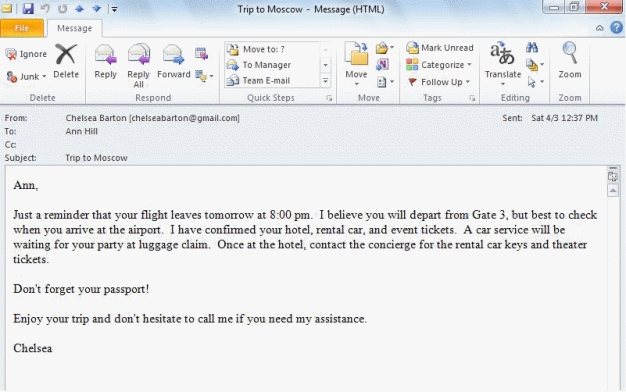 -In an e-mail message,such as the one found in the accompanying figure,the recipient's e-mail address and the message subject are found in the ____.
-In an e-mail message,such as the one found in the accompanying figure,the recipient's e-mail address and the message subject are found in the ____.
(Multiple Choice)
4.7/5  (47)
(47)
A Web server's response to a browser's request includes an HTTP ____ that indicates whether the browser's request could be fulfilled.
(Multiple Choice)
5.0/5  (41)
(41)
 -A(n)control is a program that extends the ability of the kind of applications shown in the accompanying figure to work with file formats._________________________
-A(n)control is a program that extends the ability of the kind of applications shown in the accompanying figure to work with file formats._________________________
(True/False)
4.7/5  (42)
(42)
The ____ wildcard character allows a search engine to find pages with any derivation of a basic word.
(Multiple Choice)
4.8/5  (40)
(40)
Every Web page has a unique address called a(n) Uniform Resource Locator._________________________
(True/False)
4.9/5  (41)
(41)
Technologies that create ____________________ connections include SSL/TLS and HTTPS.
(Short Answer)
4.7/5  (31)
(31)
Melissa has decided to obtain an e-mail account. Although she plans to use the e-mail account to communicate with her many friends, her main purpose in establishing it is to aid in the search for a job. She has a list of e-mail addresses for a group of potential employers. Melissa intends to e-mail her resume, along with a general message, to each of them. She will use the same message for all recipients.
-Melissa wants to ensure that the resume she attaches to the e-mail messages she is sending to the potential employers will successfully make it to them.She should try to limit the size of the attachment to ____ or less for dial-up connections.
(Multiple Choice)
4.8/5  (38)
(38)
A(n)____________________ is an advertisement that appears in a separate window when you enter a Web site.
(Short Answer)
4.7/5  (29)
(29)
Pharming is less surreptitious and easier to detect than most other hacker schemes.
(True/False)
4.7/5  (42)
(42)
Showing 81 - 100 of 150
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)