Exam 1: Computers and Digital Basics
Exam 1: Computers and Digital Basics147 Questions
Exam 2: Computer Hardware150 Questions
Exam 3: Software149 Questions
Exam 4: Operating Systems and File Management150 Questions
Exam 5: Local Area Networks150 Questions
Exam 6: The Internet149 Questions
Exam 7: The Web and E-Mail150 Questions
Exam 8: Digital Media150 Questions
Exam 9: The Computer Industry: History, careers, and Ethics150 Questions
Exam 10: Information Systems Analysis and Design150 Questions
Exam 11: Databases150 Questions
Exam 12: Computer Programming150 Questions
Select questions type
Jim has just purchased a new computer and it has made him think about how it works. He is particularly interested in how information is processed and stored in his computer. He has come to you for help.
-When adding two numbers,Jim knows that each number is going into its own register and the control unit provides the instructions such as add.He wants to know where the result of the add goes.You tell him it goes to ____.
(Multiple Choice)
4.9/5  (43)
(43)
A(n)____________________ is a type of computer that is considered one of the fastest in the world (at the time of construction).
(Short Answer)
4.9/5  (34)
(34)
Digital devices can use ____ as a code to represent character data.
(Multiple Choice)
4.8/5  (26)
(26)
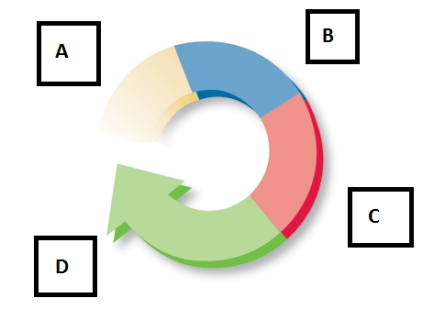 -The accompanying figure represents the instruction cycle.The second step is Box B and represents the ____.
-The accompanying figure represents the instruction cycle.The second step is Box B and represents the ____.
(Multiple Choice)
4.9/5  (33)
(33)
An ordinary personal computer that is connected to a network is a ____.
(Multiple Choice)
4.9/5  (39)
(39)
A powerful desktop computer used for high-performance tasks is a ____.
(Multiple Choice)
4.8/5  (29)
(29)
A(n)keylogger is a form of malicious code._________________________
(True/False)
4.8/5  (35)
(35)
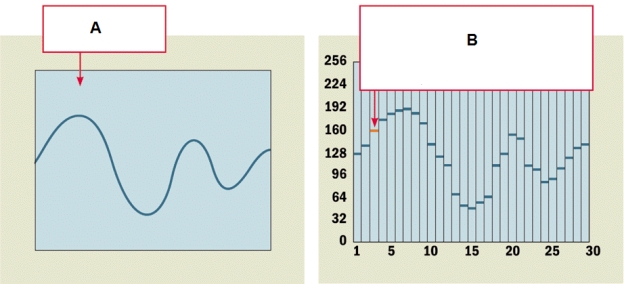 -The type of code that uses only seven bits for each character is ____.
-The type of code that uses only seven bits for each character is ____.
(Multiple Choice)
4.9/5  (41)
(41)
In terms of an authentication protocol,the phrase 'something a person is' refers to a(n)____.
(Multiple Choice)
4.9/5  (41)
(41)
A machine language instruction has two parts,the op code and the ____________________.
(Short Answer)
4.8/5  (32)
(32)
A term which can refer to a person who manipulates computers with malicious intent is ____.
(Multiple Choice)
4.8/5  (41)
(41)
____ computing provides access to information,applications,communications,and storage over the Internet.
(Multiple Choice)
5.0/5  (40)
(40)
 -The binary number 10 represents ____ in the decimal number system.
-The binary number 10 represents ____ in the decimal number system.
(Multiple Choice)
4.8/5  (41)
(41)
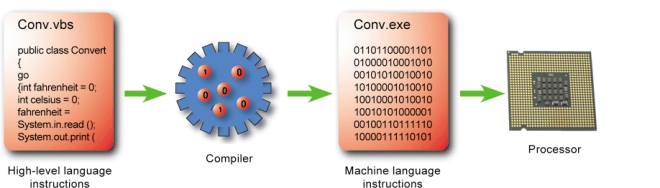 -____,as shown in the accompanying figure,can be directly executed by the processors's circuitry.
-____,as shown in the accompanying figure,can be directly executed by the processors's circuitry.
(Multiple Choice)
4.8/5  (34)
(34)
 -The accompanying figure represents the instruction cycle.The third step is Box C and represents the ____.
-The accompanying figure represents the instruction cycle.The third step is Box C and represents the ____.
(Multiple Choice)
4.9/5  (31)
(31)
A problem a hacker can cause after breaking into your computer might be ____.
(Multiple Choice)
4.8/5  (35)
(35)
The ____ phase of the digital revolution materialized in the 1990s when the Internet was opened to public use.
(Multiple Choice)
4.7/5  (39)
(39)
Showing 121 - 140 of 147
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)