Exam 7: The Web and E-Mail
Exam 1: Computers and Digital Basics147 Questions
Exam 2: Computer Hardware150 Questions
Exam 3: Software149 Questions
Exam 4: Operating Systems and File Management150 Questions
Exam 5: Local Area Networks150 Questions
Exam 6: The Internet149 Questions
Exam 7: The Web and E-Mail150 Questions
Exam 8: Digital Media150 Questions
Exam 9: The Computer Industry: History, careers, and Ethics150 Questions
Exam 10: Information Systems Analysis and Design150 Questions
Exam 11: Databases150 Questions
Exam 12: Computer Programming150 Questions
Select questions type
____ is the most frequently used HTTP method.
Free
(Multiple Choice)
5.0/5  (39)
(39)
Correct Answer:
D
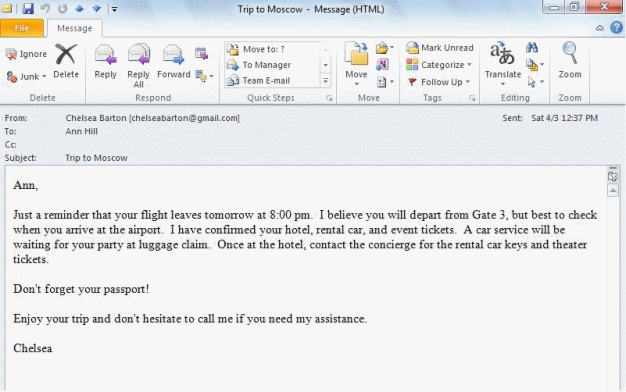 -In an e-mail message,such as the one found in the accompanying figure,the recipient's e-mail address and the message subject are found in the ____.
-In an e-mail message,such as the one found in the accompanying figure,the recipient's e-mail address and the message subject are found in the ____.
Free
(Multiple Choice)
4.8/5  (35)
(35)
Correct Answer:
B
Researchers estimate that the most extensive search engines cover less than 20% of the Web.
Free
(True/False)
4.9/5  (39)
(39)
Correct Answer:
True
In addition to using search engines,you can also find Web-based information using a(n)____ engine that searches a series of other search engines and compiles the search results.
(Multiple Choice)
4.7/5  (36)
(36)
An e-mail message in ____ format can include graphics in addition to a wide variety of fonts and font colors.
(Multiple Choice)
4.9/5  (45)
(45)
A(n)____________________ script consists of scripting statements that run on your local computer.
(Short Answer)
4.8/5  (34)
(34)
A(n)____ is a type of utility software that captures unsolicited e-mails before they reach your inbox.
(Multiple Choice)
4.9/5  (37)
(37)
As users are frequently deleting or blocking conventional cookies,marketers are turning to Flash cookies to track and target customers.
(True/False)
4.8/5  (39)
(39)
A(n)____ is client software that displays Web page elements and handles links between pages.
(Multiple Choice)
4.7/5  (32)
(32)
A(n)control is a program that extends the ability of the kind of applications shown in the accompanying figure to work with file formats._________________________
(True/False)
4.7/5  (32)
(32)
____________________ is a type of security software designed to identify and neutralize Web bugs,ad-serving cookies,and other spyware.
(Short Answer)
4.9/5  (32)
(32)
Both SSL and its successor,____,are protocols that encrypt data traveling between a client computer and an HTTP server.
(Multiple Choice)
4.8/5  (38)
(38)
A(n)____ helps people locate information on the Web by formulating simple keyword queries.
(Multiple Choice)
4.8/5  (43)
(43)
Jessica likes to participate in B2C e-commerce, but recently has had a number of friends who have had problems shopping online. She wonders if it is safe to shop online and just how much she is compromising her privacy by doing so. Jessica is justifiably worried about the security of the personal information and credit card information she regularly supplies while shopping on the Web. In addition, she knows that merchants who market goods and services over the Internet sometimes secretly gather information and provide it to advertisers or other interested parties.
-As Jessica begins her research of just how shopping carts work,she is surprised to find that many e-commerce sites store information about her Web visits on her hard drive.What do these sites use to store visit information?
(Multiple Choice)
5.0/5  (31)
(31)
HTML documents use special instructions,called HTML logos,that specify how the document should appear when displayed on a computer screen or printed._________________________
(True/False)
4.8/5  (41)
(41)
Individuals who prefer not to leave a trail of their Internet activities surf through a(n)____________________ proxy service,which uses an intermediary server to relay Web page requests after masking the originating IP address.
(Short Answer)
4.8/5  (38)
(38)
An e-mail scam designed to persuade you into revealing confidential information by replying to an e-mail is called ____.
(Multiple Choice)
4.9/5  (29)
(29)
MATCHING
Identify the letter of the choice that best matches the phrase or definition.
-A small chunk of data generated by a Web server and stored in a text file on your computer's hard disk
(Multiple Choice)
4.8/5  (44)
(44)
Showing 1 - 20 of 150
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)