Exam 5: Local Area Networks
Exam 1: Computers and Digital Basics147 Questions
Exam 2: Computer Hardware150 Questions
Exam 3: Software149 Questions
Exam 4: Operating Systems and File Management150 Questions
Exam 5: Local Area Networks150 Questions
Exam 6: The Internet149 Questions
Exam 7: The Web and E-Mail150 Questions
Exam 8: Digital Media150 Questions
Exam 9: The Computer Industry: History, careers, and Ethics150 Questions
Exam 10: Information Systems Analysis and Design150 Questions
Exam 11: Databases150 Questions
Exam 12: Computer Programming150 Questions
Select questions type
In the context of networks,the communications ____________________ refers to the set of rules for efficiently transmitting data from one network node to another.
(Short Answer)
4.9/5  (38)
(38)
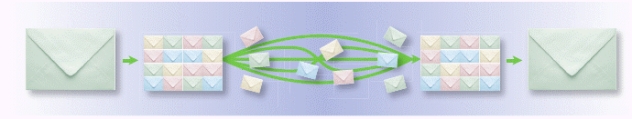 -A more efficient alternative to packet switching is shown in the accompanying figure._________________________
-A more efficient alternative to packet switching is shown in the accompanying figure._________________________
(True/False)
4.9/5  (35)
(35)
The best-known communications protocol is probably SMTP,which regulates Internet data transport._________________________
(True/False)
4.9/5  (33)
(33)
Microwaves are electromagnetic signals that can be aimed in a single direction and have more carrying capacity than radio waves._________________________
(True/False)
4.8/5  (39)
(39)
The process of converting ciphertext into plaintext is called ____.
(Multiple Choice)
4.9/5  (34)
(34)
In ____ key encryption,the key used to encrypt a message is also used to decrypt the message.
(Multiple Choice)
4.7/5  (34)
(34)
Thomas is a network expert, having mastered the finer points of network structure, topology, and geographical scope. He has built many different types of networks at home, school, and work. He is now designing a home network for his friend.
-Thomas's friend has indicated that he will accept the system that Thomas is constructing for him.However,he is concerned about security risks and wants to know what limits he can place on the system.Which of the following is NOT a true statement that Thomas can make to his friend?
(Multiple Choice)
4.9/5  (32)
(32)
A packet always travels from the source directly to the destination,never traveling through intermediate routing devices.
(True/False)
4.7/5  (42)
(42)
Which of the following is NOT an advantage of using a wired network?
(Multiple Choice)
4.9/5  (35)
(35)
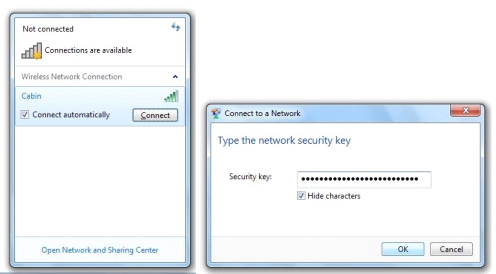 -As illustrated in the accompanying figure,Windows should automatically find the network ____ and ask you to enter the wireless encryption key or passphrase.
-As illustrated in the accompanying figure,Windows should automatically find the network ____ and ask you to enter the wireless encryption key or passphrase.
(Multiple Choice)
4.9/5  (28)
(28)
____,also referred to as personal mode,is a type of WPA used on most home networks.
(Multiple Choice)
4.9/5  (46)
(46)
If a network interface card is not built into the main system board of a computer,it can be added to a slot in the system board or to a(n)____________________ port.
(Short Answer)
4.8/5  (37)
(37)
In the early years of personal computers,networks were plentiful.
(True/False)
4.8/5  (32)
(32)
Windows automatically senses nearby networks and displays their SSIDs.
(True/False)
4.8/5  (30)
(30)
A ____ is a procedure for encrypting or decrypting a message.
(Multiple Choice)
4.8/5  (28)
(28)
Wireless ____ scrambles the data transmitted between wireless devices and then unscrambles the data only on devices that have a valid key.
(Multiple Choice)
4.8/5  (37)
(37)
Showing 41 - 60 of 150
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)