Exam 8: Controlling Information Systems: Introduction to Pervasive Controls
Exam 1: Introduction to Accounting Information Systems115 Questions
Exam 2: Enterprise Systems140 Questions
Exam 3: Electronic Business E-Business Systems113 Questions
Exam 4: Documenting Information Systems108 Questions
Exam 5: Database Management Systems180 Questions
Exam 6: Relational Databases and Sql93 Questions
Exam 7: Controlling Information Systems: Introduction to Enterprise Risk Management and Internal Control161 Questions
Exam 8: Controlling Information Systems: Introduction to Pervasive Controls157 Questions
Exam 9: Controlling Information Systems: Business Process and Application Controls126 Questions
Exam 10: The Order Entrysales Oes Process128 Questions
Exam 11: The Billingaccounts Receivable Cash Receipts Barcr Process134 Questions
Exam 12: The Purchasing Process131 Questions
Exam 13: Accounts Payablecash Disbursements Apcd Process104 Questions
Exam 14: The Human Resources Process HR Management and Payroll Processes118 Questions
Exam 15: Integrated Production Processes IPP106 Questions
Exam 16: General Ledger and Business Reporting Glbr Process78 Questions
Exam 17: Acquiring and Implementing Accounting Information Systems206 Questions
Select questions type
____________________ documentation provides a description of an application computer program and usually includes the program's purpose, program flowcharts, and source code listings.
(Short Answer)
4.9/5  (36)
(36)
Segregation of duties consists of separating the four functions of authorizing events, ____________________ events, ____________________ events, and safeguarding the resources resulting from consummating the events.
(Short Answer)
4.8/5  (36)
(36)
Which of the following has the responsibility to ensure the security of all IT resources?
(Multiple Choice)
4.9/5  (48)
(48)
Which of the following has the major duties of prioritizing and selecting IT projects and resources
(Multiple Choice)
4.8/5  (39)
(39)
The first list below contains 10 control plans discussed in Chapter 8.The second list describes 10 system failures that have control implications.Required:
On the answer line to the left of each system failure, insert the capital letter from the first list of the best control plan to prevent the system failure from occurring.(If you can't find a control that will prevent the failure, then choose a detective or corrective control plan).A letter should be used only once.Control Plans


(Essay)
4.8/5  (43)
(43)
Program change controls provide assurance that all modifications to programs are authorized and that the changes are completed, tested, and properly implemented.
(True/False)
4.9/5  (32)
(32)
A key control concern is that certain people within an organization have easy access to applications programs and data files.The people are:
(Multiple Choice)
4.8/5  (34)
(34)
Application documentation that describes the application and contains instructions for preparing inputs and using outputs is a(n):
(Multiple Choice)
4.7/5  (40)
(40)
Combining the functions of authorizing and executing events is a violation of the organizational control plan known as ______________________________.
(Short Answer)
4.9/5  (35)
(35)
This logs and monitors who is on or trying to access an organization's network.
(Multiple Choice)
4.9/5  (45)
(45)
Training materials help users learn their jobs and perform consistently in those jobs.
(True/False)
4.8/5  (41)
(41)
The four events-processing functions that constitute the segregation of duties control plan are:
 Required:
Below is a list of ten events-processing activities, five relating to the cycle of activities involved in processing a sales event and seven relating to the cycle for a purchase event.Classify each of the twelve activities into one of the four functional categories listed above by placing the letter A, B, C, or D on the answer line to the left of each number.You should use only one letter for each of the answers.
Required:
Below is a list of ten events-processing activities, five relating to the cycle of activities involved in processing a sales event and seven relating to the cycle for a purchase event.Classify each of the twelve activities into one of the four functional categories listed above by placing the letter A, B, C, or D on the answer line to the left of each number.You should use only one letter for each of the answers. 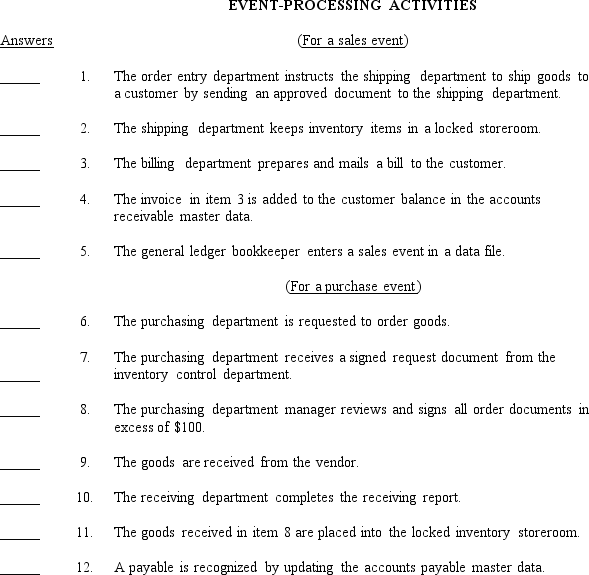
(Essay)
4.8/5  (36)
(36)
____________________ is any fraud committed by two or more individuals or departments.
(Short Answer)
4.8/5  (38)
(38)
____________________ identification systems identify authorized personnel through some unique physical trait such as fingers, hands, voice, eyes, face, and writing dynamics.
(Short Answer)
4.9/5  (41)
(41)
The data entry clerk types data from an order form into an on-line computer through a pre-formatted screen.This is an example of:
(Multiple Choice)
4.8/5  (28)
(28)
In an information systems organizational structure, the function of ____ is the central point from which to control data and is a central point of vulnerability.
(Multiple Choice)
4.9/5  (40)
(40)
Individual departments coordinate the organizational and IT strategic planning processes and reviews and approves the strategic IT plan.
(True/False)
4.8/5  (47)
(47)
The function composed of people, procedures, and equipment that is typically called the information systems department, IS department, or IT department is the _____________________________________________.
(Short Answer)
4.9/5  (43)
(43)
Showing 61 - 80 of 157
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)