Multiple Choice
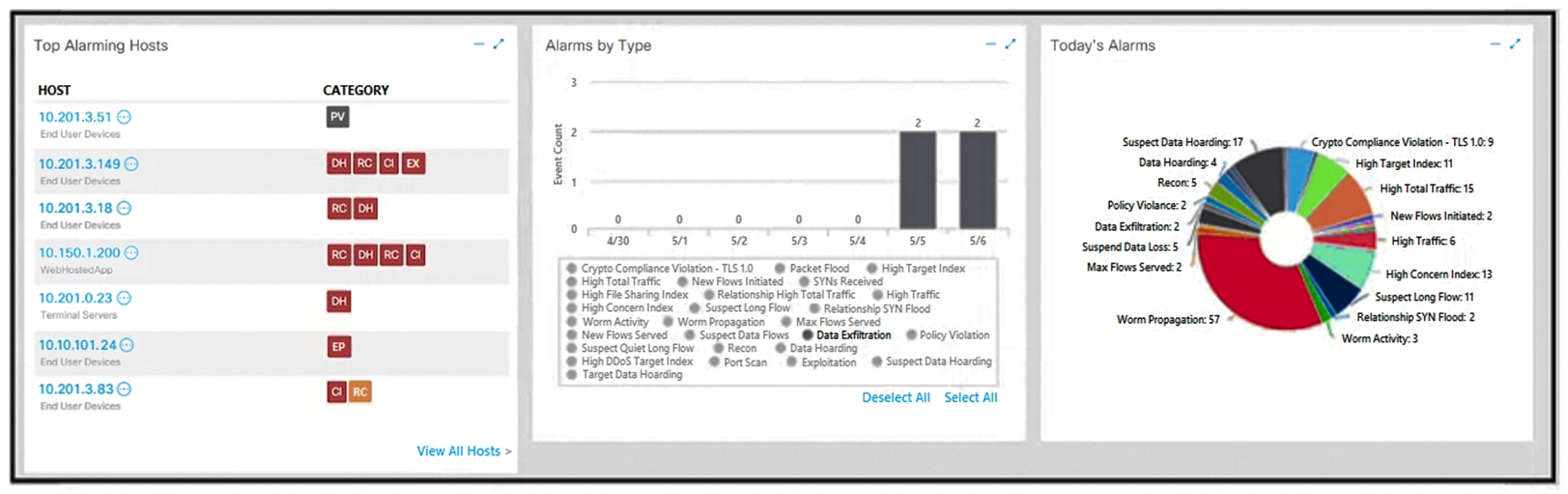 Refer to the exhibit. What is the potential threat identified in this Stealthwatch dashboard?
Refer to the exhibit. What is the potential threat identified in this Stealthwatch dashboard?
A) A policy violation is active for host 10.10.101.24.
B) A host on the network is sending a DDoS attack to another inside host.
C) There are two active data exfiltration alerts.
D) A policy violation is active for host 10.201.3.149.
Correct Answer:

Verified
Correct Answer:
Verified
Q69: Which action should be taken if the
Q70: What is a difference between tampered and
Q71: During which phase of the forensic process
Q72: Which category relates to improper use or
Q73: What should a security analyst consider when
Q75: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q76: Which security technology allows only a set
Q77: What does cyber attribution identify in an
Q78: What is a benefit of agent-based protection
Q79: A SOC analyst is investigating an incident