Multiple Choice
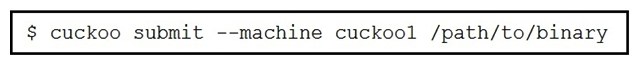 Refer to the exhibit. Which event is occurring?
Refer to the exhibit. Which event is occurring?
A) A binary named "submit" is running on VM cuckoo1.
B) A binary is being submitted to run on VM cuckoo1
C) A binary on VM cuckoo1 is being submitted for evaluation
D) A URL is being evaluated to see if it has a malicious binary
Correct Answer:

Verified
Correct Answer:
Verified
Q70: What is a difference between tampered and
Q71: During which phase of the forensic process
Q72: Which category relates to improper use or
Q73: What should a security analyst consider when
Q74: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q76: Which security technology allows only a set
Q77: What does cyber attribution identify in an
Q78: What is a benefit of agent-based protection
Q79: A SOC analyst is investigating an incident
Q80: What is the difference between deep packet