Multiple Choice
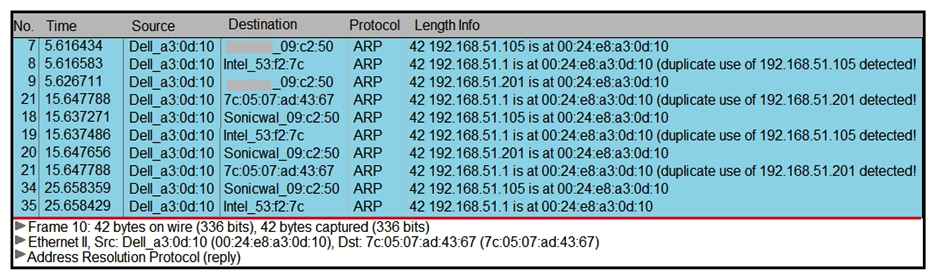 Refer to the exhibit. A security analyst notices unusual connections while monitoring traffic. What is the attack vector, and which action should be taken to prevent this type of event?
Refer to the exhibit. A security analyst notices unusual connections while monitoring traffic. What is the attack vector, and which action should be taken to prevent this type of event?
A) DNS spoofing; encrypt communication protocols
B) SYN flooding, block malicious packets
C) ARP spoofing; configure port security
D) MAC flooding; assign static entries
Correct Answer:

Verified
Correct Answer:
Verified
Q8: A scanner detected a malware-infected file on
Q9: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q10: A security team receives reports of multiple
Q11: Which technique is used to evade detection
Q12: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q14: A security team is discussing lessons learned
Q15: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q16: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q17: A security team received an alert of
Q18: An engineer received a call to assist