Multiple Choice
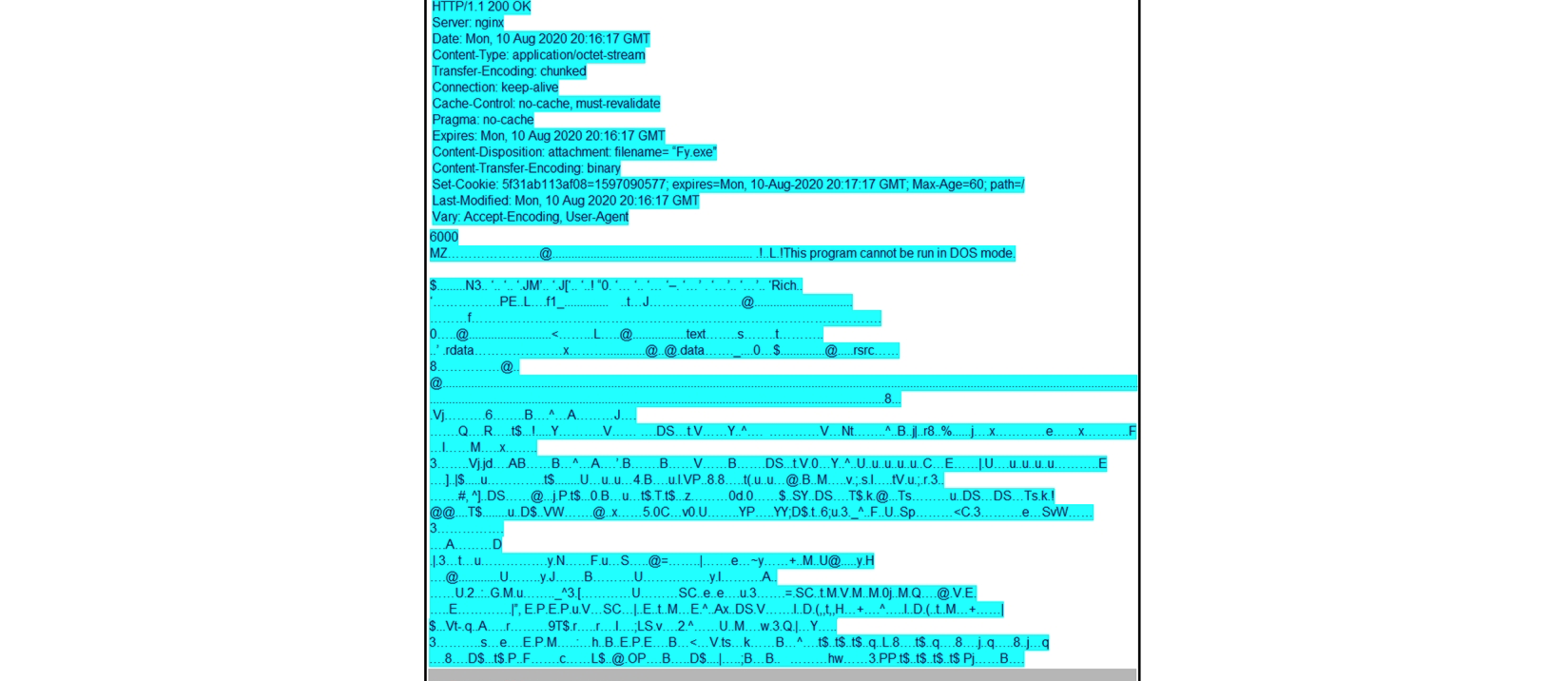 Refer to the exhibit. According to the Wireshark output, what are two indicators of compromise for detecting an Emotet malware download? (Choose two.)
Refer to the exhibit. According to the Wireshark output, what are two indicators of compromise for detecting an Emotet malware download? (Choose two.)
A) Domain name:iraniansk.com
B) Server: nginx
C) Hash value: 5f31ab113af08=1597090577
D) filename= "Fy.exe"
E) Content-Type: application/octet-stream
Correct Answer:

Verified
Correct Answer:
Verified
Q11: Which technique is used to evade detection
Q12: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q13: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q14: A security team is discussing lessons learned
Q15: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q17: A security team received an alert of
Q18: An engineer received a call to assist
Q19: A website administrator has an output of
Q20: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q21: Which magic byte indicates that an analyzed