Multiple Choice
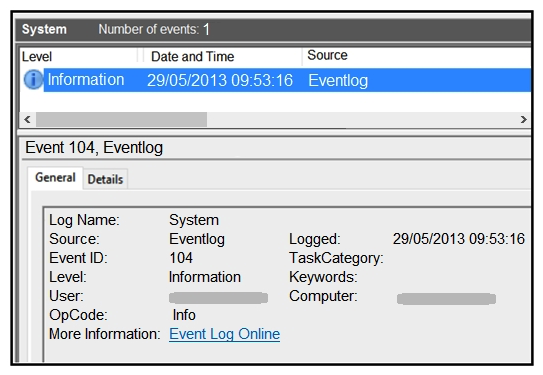 Refer to the exhibit. An employee notices unexpected changes and setting modifications on their workstation and creates an incident ticket. A support specialist checks processes and services but does not identify anything suspicious. The ticket was escalated to an analyst who reviewed this event log and also discovered that the workstation had multiple large data dumps on network shares. What should be determined from this information?
Refer to the exhibit. An employee notices unexpected changes and setting modifications on their workstation and creates an incident ticket. A support specialist checks processes and services but does not identify anything suspicious. The ticket was escalated to an analyst who reviewed this event log and also discovered that the workstation had multiple large data dumps on network shares. What should be determined from this information?
A) data obfuscation
B) reconnaissance attack
C) brute-force attack
D) log tampering
Correct Answer:

Verified
Correct Answer:
Verified
Q15: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q16: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q17: A security team received an alert of
Q18: An engineer received a call to assist
Q19: A website administrator has an output of
Q20: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q21: Which magic byte indicates that an analyzed
Q22: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q23: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q25: Which tool conducts memory analysis?<br>A) MemDump<br>B) Sysinternals