Multiple Choice
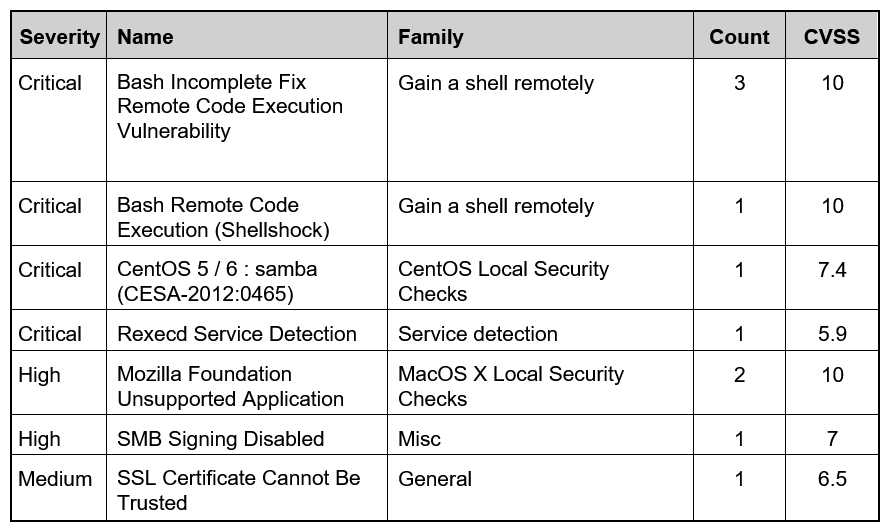 Refer to the exhibit. Based on the detected vulnerabilities, what is the next recommended mitigation step?
Refer to the exhibit. Based on the detected vulnerabilities, what is the next recommended mitigation step?
A) Evaluate service disruption and associated risk before prioritizing patches.
B) Perform root cause analysis for all detected vulnerabilities.
C) Remediate all vulnerabilities with descending CVSS score order.
D) Temporarily shut down unnecessary services until patch deployment ends.
Correct Answer:

Verified
Correct Answer:
Verified
Q80: Refer to the exhibit. A security analyst
Q81: How does Wireshark decrypt TLS network traffic?<br>A)
Q82: A security engineer discovers that a spreadsheet
Q83: An organization had several cyberattacks over the
Q84: A company recently completed an internal audit
Q86: An organization installed a new application server
Q87: According to GDPR, what should be done
Q88: An engineer receives an incident ticket with
Q89: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q90: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the