Multiple Choice
Refer to the exhibit. A security analyst needs to investigate a security incident involving several suspicious connections with a possible attacker. Which tool should the analyst use to identify the source IP of the offender? 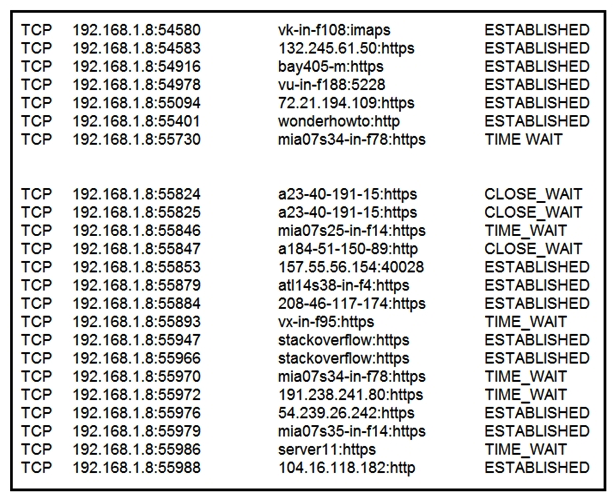
A) packet sniffer
B) malware analysis
C) SIEM
D) firewall manager
Correct Answer:

Verified
Correct Answer:
Verified
Q75: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q76: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q77: A threat actor has crafted and sent
Q78: An organization suffered a security breach in
Q79: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q81: How does Wireshark decrypt TLS network traffic?<br>A)
Q82: A security engineer discovers that a spreadsheet
Q83: An organization had several cyberattacks over the
Q84: A company recently completed an internal audit
Q85: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the