Multiple Choice
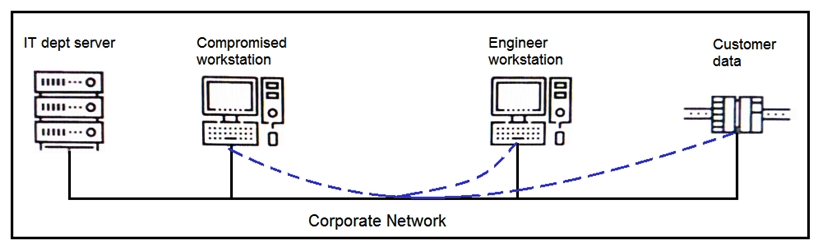 Refer to the exhibit. An engineer received a report that an attacker has compromised a workstation and gained access to sensitive customer data from the network using insecure protocols. Which action prevents this type of attack in the future?
Refer to the exhibit. An engineer received a report that an attacker has compromised a workstation and gained access to sensitive customer data from the network using insecure protocols. Which action prevents this type of attack in the future?
A) Use VLANs to segregate zones and the firewall to allow only required services and secured protocols
B) Deploy a SOAR solution and correlate log alerts from customer zones
C) Deploy IDS within sensitive areas and continuously update signatures
D) Use syslog to gather data from multiple sources and detect intrusion logs for timely responses
Correct Answer:

Verified
Correct Answer:
Verified
Q74: A cloud engineer needs a solution to
Q75: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q76: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q77: A threat actor has crafted and sent
Q78: An organization suffered a security breach in
Q80: Refer to the exhibit. A security analyst
Q81: How does Wireshark decrypt TLS network traffic?<br>A)
Q82: A security engineer discovers that a spreadsheet
Q83: An organization had several cyberattacks over the
Q84: A company recently completed an internal audit