Multiple Choice
A security analyst is conducting a post-incident log analysis to determine which indicators can be used to detect further occurrences of a data exfiltration incident. The analyst determines backups were not performed during this time and reviews the following: 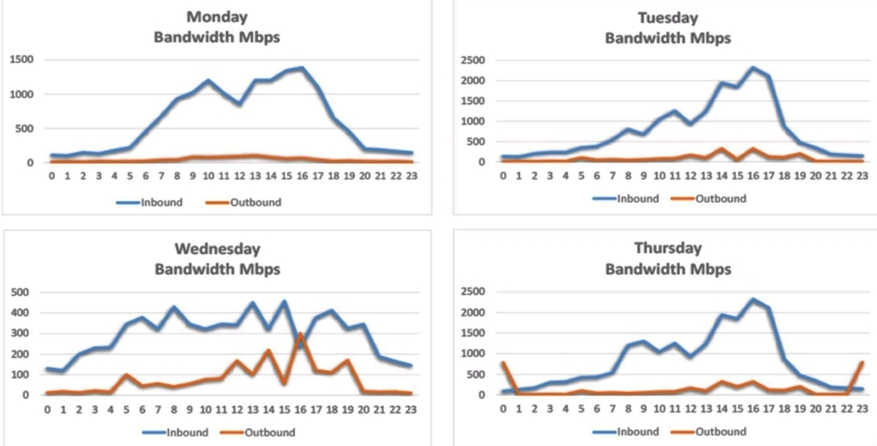 Which of the following should the analyst review to find out how the data was exfiltrated?
Which of the following should the analyst review to find out how the data was exfiltrated?
A) Monday's logs
B) Tuesday's logs
C) Wednesday's logs
D) Thursday's logs
Correct Answer:

Verified
Correct Answer:
Verified
Q68: A threat feed notes malicious actors have
Q69: A finance department employee has received a
Q70: A Chief Information Security Officer (CISO) is
Q71: A network attack that is exploiting a
Q72: A cybersecurity analyst is supporting an incident
Q74: A cybersecurity analyst needs to rearchitect the
Q75: A security analyst is evaluating two vulnerability
Q76: Which of the following types of policies
Q77: An information security analyst is compiling data
Q78: A company was recently awarded several large