Multiple Choice
A security analyst is evaluating two vulnerability management tools for possible use in an organization. The analyst set up each of the tools according to the respective vendor's instructions and generated a report of vulnerabilities that ran against the same target server. Tool A reported the following: 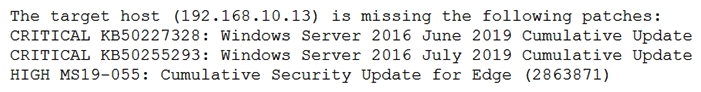 Tool B reported the following:
Tool B reported the following:  Which of the following BEST describes the method used by each tool? (Choose two.)
Which of the following BEST describes the method used by each tool? (Choose two.)
A) Tool A is agent based.
B) Tool A used fuzzing logic to test vulnerabilities.
C) Tool A is unauthenticated.
D) Tool B utilized machine learning technology.
E) Tool B is agent based.
F) Tool B is unauthenticated.
Correct Answer:

Verified
Correct Answer:
Verified
Q70: A Chief Information Security Officer (CISO) is
Q71: A network attack that is exploiting a
Q72: A cybersecurity analyst is supporting an incident
Q73: A security analyst is conducting a post-incident
Q74: A cybersecurity analyst needs to rearchitect the
Q76: Which of the following types of policies
Q77: An information security analyst is compiling data
Q78: A company was recently awarded several large
Q79: During an investigation, a security analyst determines
Q80: A developer wrote a script to make