Essay
Computer crime taxonomy, computer criminals and internal controls
For each independent situation below, indicate: (a) the type of computer crime based on Carter's taxonomy, (b) the type of computer criminal and (c) one internal control that would address the crime. Note to instructor: The situations in this problem are different from those in Problem 7. 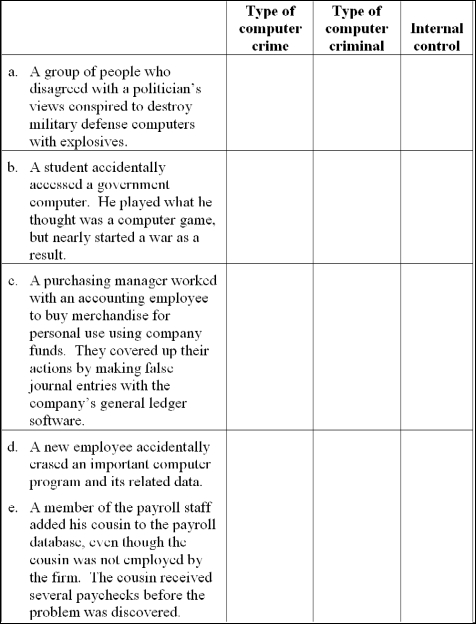
Correct Answer:

Verified
Correct Answer:
Verified
Q48: As a business risk, extortion can be
Q49: According to the COBIT accountability framework, the
Q50: According to Carter's taxonomy of computer crime,
Q51: The COBIT framework can be used to
Q52: Identify the type of computer criminal described
Q53: Which type of computer criminal is least
Q54: According to Carter's taxonomy of computer crime,
Q55: Administrative security controls can be used to
Q56: A customer's bank account should be credited
Q57: Which type of internal control is most