Exam 11: Computer Crime and Information Technology Security
Exam 1: Role and Purpose of Accounting Information Systems61 Questions
Exam 2: Transaction Processing in the Ais59 Questions
Exam 3: Internal Controls61 Questions
Exam 4: Management Concepts61 Questions
Exam 5: Information Systems Concepts60 Questions
Exam 6: Flowcharting61 Questions
Exam 7: Data Flow Diagramming63 Questions
Exam 8: Rea Modeling62 Questions
Exam 9: XBRL63 Questions
Exam 10: E-Business and Enterprise Resource Planning Systems65 Questions
Exam 11: Computer Crime and Information Technology Security63 Questions
Exam 12: Salescollection Process64 Questions
Exam 13: Acquisitionpayment Process64 Questions
Exam 14: Other Business Processes61 Questions
Exam 15: Decision-Making Models and Knowledge Management62 Questions
Exam 16: Professionalism, Ethics, and Career Planning58 Questions
Exam 17: Auditing and Evaluating the Ais59 Questions
Select questions type
In your own words, explain the relationship between each of the following groups found in the CoBIT accountability framework:
A. Audit committee, external audit
b. Board of directors, IT and information security management
c. Employees, board of directors
(Essay)
4.8/5  (41)
(41)
The CoBIT framework identifies seven information criteria; the FASB conceptual framework includes four qualitative characteristics of accounting information, as well as several assumptions, principles and constraints. Which of the following statements about them is most true?
(Multiple Choice)
4.9/5  (35)
(35)
Computer crimes that fall under Carter's "target" category are most closely associated with which generic element of an accounting information system?
(Multiple Choice)
4.9/5  (41)
(41)
The chapter discussed seven types of computer criminals and eleven examples of risks and threats to information systems. Consider the items below, each of which pairs a type of computer criminal with a risk; provide a specific example based on both items.
A. Organized crime, extortion
b. Terrorist, service interruption / delay
c. Insider, error
d. Cyber-criminal, information theft
(Essay)
4.8/5  (29)
(29)
The terms target, instrumentality, incidental and associated from Carter's taxonomy are most closely associated with which form of risk from Brown's taxonomy?
(Multiple Choice)
4.9/5  (48)
(48)
Disclosure of confidential information is one risk associated with information technology. Which of the following would be considered confidential information?
(Multiple Choice)
4.9/5  (45)
(45)
Which element of Carter's taxonomy of computer crime is associated with each item below?
A. Computer is not required for the crime but is related to the criminal act
b. Computer is used to commit the crime
c. Computer use may make a crime more difficult to trace
d. Growth of the Internet creates new ways of reaching victims
e. Objective is to impact the confidentiality, availability and / or integrity of data
f. Presence of computers has generated new versions of fairly traditional crimes
g. Targets the system or its data
h. Technological growth creates new crime targets
i. Use of the computer simplifies criminal actions
j. Uses the computer to further a criminal end
(Essay)
4.8/5  (32)
(32)
According to Carter's taxonomy, use of a computer to further a criminal end refers to which of the following categories?
(Multiple Choice)
4.8/5  (24)
(24)
Consider the following short case as you respond to the next question: Melissa is an internal auditor for the County of Bufflufia. Her job responsibilities include providing training on information systems security and checking the work of data entry clerks. Melissa is also part of a team that responds to denial-of-service attacks on the county's information system. Her co-worker, Eugene, ensures that all the county's computers have the most up-to-date antivirus software; he also enforces the county's policy of backing up sensitive data, such as employee social security numbers and other payroll information, at least once a day. The back-ups are dated and stored in a locked filing cabinet.Which of the following statements is most true?
(Multiple Choice)
4.8/5  (34)
(34)
Consider the following list as you respond to the next question: i. An individual broke into a retail store's information system, stealing sensitive employee information
Ii) A flaw in a computer's operating system allowed a competitor to steal information about new products
Iii) A thief sat outside a bank, capturing clients' information as they used the ATM. The thief later sold that information to a gang.iv. A group of criminals in three different countries sent fraudulent e-mails to individuals in a fourth country in an effort to defraud them.Which of the following statements is most true?
(Multiple Choice)
4.8/5  (32)
(32)
The CoBIT framework identifies seven information criteria. In each example below, indicate one criterion that is met AND one that is not met in the space provided. 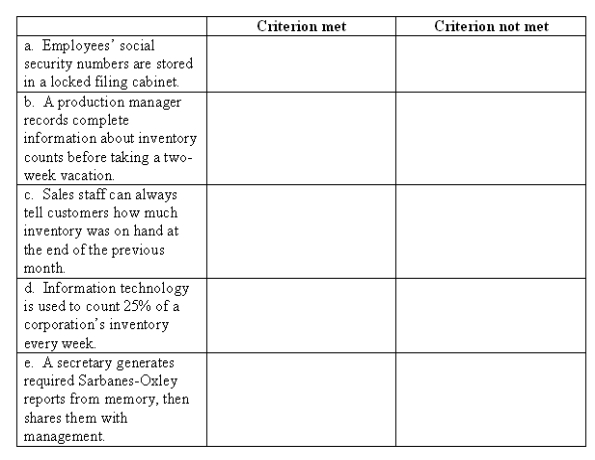
(Essay)
4.8/5  (38)
(38)
BSD Corporation developed an internal control plan using the COSO framework. Based on the CoBIT accountability framework, which of the following statements is most true?
(Multiple Choice)
4.7/5  (40)
(40)
George received an e-mail that threatened to release his personal financial data unless he paid a fee. That situation is an example of:
(Multiple Choice)
4.8/5  (36)
(36)
Consider the following list as you respond to the next question: i. An individual broke into a retail store's information system, stealing sensitive employee information
Ii) A flaw in a computer's operating system allowed a competitor to steal information about new products
Iii) A thief sat outside a bank, capturing clients' information as they used the ATM. The thief later sold that information to a gang.iv. A group of criminals in three different countries sent fraudulent e-mails to individuals in a fourth country in an effort to defraud them.Which items in the list are examples of organized crime?
(Multiple Choice)
4.7/5  (29)
(29)
Which category of computer crime in Carter's taxonomy recognizes that the presence of computers has generated new versions of traditional crimes?
(Multiple Choice)
4.9/5  (38)
(38)
Which type of computer criminal is likely to launch a denial-of-service attack?
(Multiple Choice)
4.8/5  (41)
(41)
Jack conducted an Internet search for examples of computer crime that resulted in the items listed below. Which type of computer criminal is described in each? Be as specific as possible in your responses.
A. Boris and Natasha coordinated ten people who sent out e-mails asking the recipients to purchase fake lottery tickets.
B. Gil, an IT consultant for DMM Corporation, stole personal information about corporate executives and sold it to tabloid newspapers.
C. Marie, the chief information officer of RBC Corporation, planted a logic bomb in case she ever lost her job.
D. Timothy shut down traffic lights on a major street in his city in an effort to cause serious traffic accidents.
E. Zachary used a computer program he found on the Internet to "kill" characters in an online game.
(Essay)
4.9/5  (41)
(41)
WER Corporation forces its employees to change their system password every six months. Which type of security control best describes the company's policy?
(Multiple Choice)
4.9/5  (41)
(41)
Malicious software, such as a logic bomb, is most closely related to which generic element of the accounting information system?
(Multiple Choice)
4.9/5  (35)
(35)
Showing 21 - 40 of 63
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)