Exam 11: Computer Crime and Information Technology Security
Exam 1: Role and Purpose of Accounting Information Systems61 Questions
Exam 2: Transaction Processing in the Ais59 Questions
Exam 3: Internal Controls61 Questions
Exam 4: Management Concepts61 Questions
Exam 5: Information Systems Concepts60 Questions
Exam 6: Flowcharting61 Questions
Exam 7: Data Flow Diagramming63 Questions
Exam 8: Rea Modeling62 Questions
Exam 9: XBRL63 Questions
Exam 10: E-Business and Enterprise Resource Planning Systems65 Questions
Exam 11: Computer Crime and Information Technology Security63 Questions
Exam 12: Salescollection Process64 Questions
Exam 13: Acquisitionpayment Process64 Questions
Exam 14: Other Business Processes61 Questions
Exam 15: Decision-Making Models and Knowledge Management62 Questions
Exam 16: Professionalism, Ethics, and Career Planning58 Questions
Exam 17: Auditing and Evaluating the Ais59 Questions
Select questions type
The CoBIT framework looks at the issue of internal control from three points of view. An organization's hardware and software configuration is most closely related to:
(Multiple Choice)
4.7/5  (33)
(33)
The CoBIT framework is divided into four domains of knowledge. Suppose TPC Corporation uses the systems development life cycle for new IT projects. Which of the following statements is most true?
(Multiple Choice)
4.8/5  (33)
(33)
An information systems development company routinely creates a password that they do not disclose to their clients. In that way, the development company can bypass any security the client adds on later if the system needs maintenance. The client's information system is therefore at greatest risk for:
(Multiple Choice)
4.7/5  (43)
(43)
Consider the following examples of computer crime as you answer the next question: i. Social Security numbers are stolen from a company's database.ii. A fraudster uses a computer to identify people over the age of 80 with annual incomes of $250,000 or more
Iii) An employee receives threats from a co-worker via e-mail
Iv) An unhappy customer launches a denial-of-service attack
Carter's taxonomy of computer crime comprises four categories. Which of the following pairs includes two items from the same category?
(Multiple Choice)
4.8/5  (36)
(36)
The CoBIT framework looks at the issue of internal control from three points of view. If NTS Corporation's strategic plan includes a statement about planned increases in sales, which of the following statements is most true?
(Multiple Choice)
4.7/5  (34)
(34)
The chapter discussed the four elements of Carter's taxonomy of computer crime, eleven business risks / threats to information systems and seven common types of computer criminals. Classify each item below using each of them. 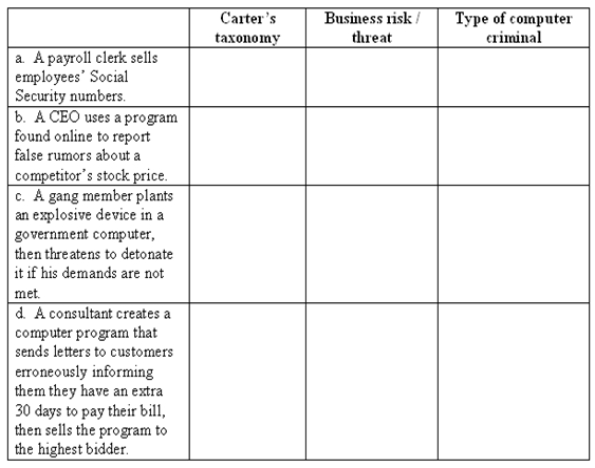
(Essay)
4.8/5  (40)
(40)
Based on the CoBIT accountability framework, which of the following statements is most true?
(Multiple Choice)
4.7/5  (45)
(45)
The risk of disclosure of confidential information is most closely related to which category in Carter's taxonomy?
(Multiple Choice)
4.9/5  (34)
(34)
The CoBIT framework is divided into four domains of knowledge; the text discussed three types of controls related to information security. Which of the following statements is most true?
(Multiple Choice)
4.9/5  (37)
(37)
Based on the list provided in the text, indicate the type of computer criminal described in each of the following.
A. A young, inexperienced hacker who uses tools written by others for the purpose of attacking systems
b. Could seriously disrupt power grids, telecommunications and transportation
c. Hackers driven by financial gain
d. Recruit talented hackers to handle the technical aspects of crime
e. Someone who invades an information system for malicious purposes
f. Take advantage of networked systems by turning to computer intrusion techniques to gather the information they desire
g. The largest threat to a company's information systems
(Essay)
4.7/5  (34)
(34)
The CoBIT framework identifies seven information criteria; the FASB conceptual framework includes four qualitative characteristics of accounting information, as well as several assumptions, principles and constraints. Which of the following statements about them is most true?
(Multiple Choice)
4.9/5  (37)
(37)
Ethan is an information technology security consultant. He has been asked to speak to a local professional organization about ways to strengthen internal controls against computer crime, and wants to relate his comments to the CoBIT framework. Prepare a short summary of the key points Ethan should make in his presentation; ensure that each one has a clear relationship to the CoBIT framework.
(Essay)
4.8/5  (38)
(38)
The CoBIT framework discusses seven information criteria. Consider the pairs of items below; which one violates the criterion indicated?
(Multiple Choice)
4.9/5  (30)
(30)
Consider the following short case as you respond to the next question: Melissa is an internal auditor for the County of Bufflufia. Her job responsibilities include providing training on information systems security and checking the work of data entry clerks. Melissa is also part of a team that responds to denial-of-service attacks on the county's information system. Her co-worker, Eugene, ensures that all the county's computers have the most up-to-date antivirus software; he also enforces the county's policy of backing up sensitive data, such as employee social security numbers and other payroll information, at least once a day. The back-ups are dated and stored in a locked filing cabinet.Which employee has responsibilities related to all three elements of the CIA triad?
(Multiple Choice)
4.7/5  (32)
(32)
CoBIT's information criteria include all of the following except:
(Multiple Choice)
4.9/5  (34)
(34)
An organization that uses the CoBIT framework to strengthen internal controls wants to improve the confidentiality of its information. Which of the following internal controls will best help achieve that goal?
(Multiple Choice)
4.9/5  (28)
(28)
Business risks and threats to information systems include all of the following except:
(Multiple Choice)
4.9/5  (34)
(34)
Which of the following types of computer criminal is least likely to be motivated by financial gain?
(Multiple Choice)
4.9/5  (30)
(30)
PCA Corporation maintains its fixed asset records in an Excel spreadsheet, as well as in its general ledger software. An internal auditor for PCA downloaded the Excel spreadsheet, then verified the information in it against both the general ledger software and the actual fixed assets in use. Which of the following statements is most true?
(Multiple Choice)
4.7/5  (33)
(33)
Showing 41 - 60 of 63
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)