Exam 9: Data Design
Exam 1: Introduction to Systems Analysis and Design80 Questions
Exam 2: Analyzing the Business Case81 Questions
Exam 3: Managing Systems Projects78 Questions
Exam 4: Requirements Modeling98 Questions
Exam 5: Data and Process Modeling84 Questions
Exam 6: Object Modeling78 Questions
Exam 7: Development Strategies82 Questions
Exam 8: User Interface Design82 Questions
Exam 9: Data Design86 Questions
Exam 10: System Architecture78 Questions
Exam 11: Managing Systems Implementation81 Questions
Exam 12: Managing Systems Support and Security81 Questions
Exam 13: Appendix-The Systems Analyst’s Toolkit45 Questions
Exam 14: CASE Tools45 Questions
Exam 15: Financial Analysis Tools45 Questions
Exam 16: Internet Resource Tools44 Questions
Select questions type
_____, a coding method that uses one byte per character, is used on most personal computers.
Free
(Multiple Choice)
4.9/5  (40)
(40)
Correct Answer:
A
Migrating a traditional database design to the web can require design modification, additional software, and some added expense.
Free
(True/False)
4.9/5  (31)
(31)
Correct Answer:
False
A _____, which is a framework for organizing, storing, and managing data, consists of files or tables that interact in various ways.
Free
(Multiple Choice)
4.7/5  (38)
(38)
Correct Answer:
A
Matching
Identify the letters of the choices that best match the phrases or definitions.
-A widely used method of visualizing and documenting software systems design
(Multiple Choice)
4.8/5  (36)
(36)
The data mining technique that relies on association rule learning is often called _____.
(Multiple Choice)
4.8/5  (46)
(46)
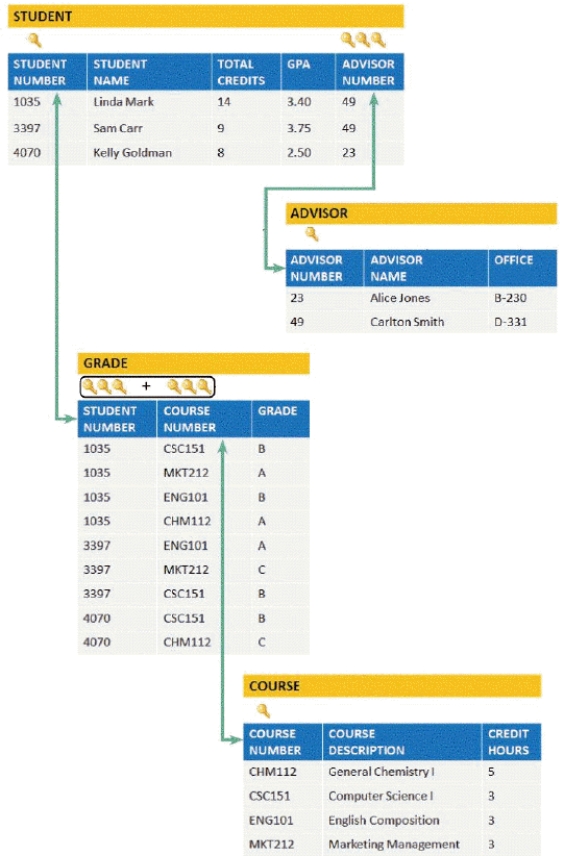 -In the accompanying figure, a _____ is a field or combination of fields that uniquely and minimally identifies a particular member of an entity.
-In the accompanying figure, a _____ is a field or combination of fields that uniquely and minimally identifies a particular member of an entity.
(Multiple Choice)
4.8/5  (33)
(33)
 -A _____, which is not unique, is a field or combination of fields that can be used to access or retrieve records.
-A _____, which is not unique, is a field or combination of fields that can be used to access or retrieve records.
(Multiple Choice)
4.8/5  (31)
(31)
A repeating group is a set of one or more fields that can occur only once in a single record, with each occurrence having the same value.
(True/False)
4.9/5  (35)
(35)
Web-based designs are dependent on a specific combination of hardware and software.
(True/False)
4.9/5  (36)
(36)
_____ is the process of converting readable data into unreadable characters to prevent unauthorized access to the data.
(Multiple Choice)
4.8/5  (25)
(25)
Matching
Identify the letters of the choices that best match the phrases or definitions.
-A kind of storage that refers to data that a user can view, regardless of how or where the information actually is organized or stored
(Multiple Choice)
4.7/5  (31)
(31)
_____ enables Java applications to exchange data with any database that uses SQL statements and is compliant with its standard.
(Multiple Choice)
4.8/5  (40)
(40)
 -In the accompanying figure, any field that serves as a primary key is called a _____.
-In the accompanying figure, any field that serves as a primary key is called a _____.
(Multiple Choice)
4.8/5  (35)
(35)
_____, a coding method that uses one byte per character, is used on mainframe computers and high-capacity servers.
(Multiple Choice)
4.7/5  (37)
(37)
Case 9-2
Emily is functioning with her customer, Anna, on the design of a new database. She describes to Anna that key fields are utilized to access, coordinate, and preserve the data records.
-Anna asks if it is manageable to fetch records using a field or combination of fields that is not unique. Emily tells her that it is possible using one type of key. Identify the type of key used here.
(Multiple Choice)
4.9/5  (44)
(44)
In a web-based design, the Internet serves as the _____ for the database management system.
(Multiple Choice)
4.7/5  (34)
(34)
Matching
Identify the letters of the choices that best match the phrases or definitions.
-A set of rules that avoids data inconsistency and quality problems
(Multiple Choice)
4.8/5  (38)
(38)
EBCDIC and ASCII both require _____ bits for storage of each character.
(Multiple Choice)
4.8/5  (37)
(37)
Showing 1 - 20 of 86
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)