Exam 12: Managing Systems Support and Security
Exam 1: Introduction to Systems Analysis and Design80 Questions
Exam 2: Analyzing the Business Case81 Questions
Exam 3: Managing Systems Projects78 Questions
Exam 4: Requirements Modeling98 Questions
Exam 5: Data and Process Modeling84 Questions
Exam 6: Object Modeling78 Questions
Exam 7: Development Strategies82 Questions
Exam 8: User Interface Design82 Questions
Exam 9: Data Design86 Questions
Exam 10: System Architecture78 Questions
Exam 11: Managing Systems Implementation81 Questions
Exam 12: Managing Systems Support and Security81 Questions
Exam 13: Appendix-The Systems Analyst’s Toolkit45 Questions
Exam 14: CASE Tools45 Questions
Exam 15: Financial Analysis Tools45 Questions
Exam 16: Internet Resource Tools44 Questions
Select questions type
_____ prevents unauthorized users from creating, modifying, or deleting information.
Free
(Multiple Choice)
4.9/5  (36)
(36)
Correct Answer:
B
A _____ is a security weakness or soft spot.
Free
(Multiple Choice)
4.9/5  (38)
(38)
Correct Answer:
B
Perfective maintenance usually is cost effective _____ a system's operational life.
Free
(Multiple Choice)
4.8/5  (31)
(31)
Correct Answer:
B
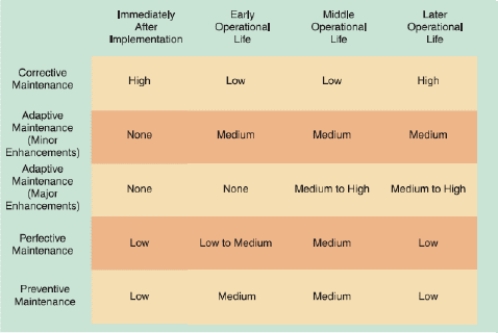 -As shown in the accompanying figure, once a system becomes stable, maintenance costs usually remain low and involve minor _____ maintenance.
-As shown in the accompanying figure, once a system becomes stable, maintenance costs usually remain low and involve minor _____ maintenance.
(Multiple Choice)
4.9/5  (29)
(29)
A _____ is the main line of defense between a local network, or intranet, and the Internet.
(Multiple Choice)
4.8/5  (37)
(37)
Matching
Identify the letters of the choices that best match the phrases or definitions.
-Records everything that is typed into the keyboard, including passwords, while the system continues to function normally
(Multiple Choice)
4.8/5  (30)
(30)
_____ expenses vary significantly during a system's operational life and include spending to support maintenance activities.
(Multiple Choice)
4.8/5  (34)
(34)
Matching
Identify the letters of the choices that best match the phrases or definitions.
-A risk control strategy that reduces the impact of a risk by careful planning and preparation
(Multiple Choice)
4.8/5  (36)
(36)
_____ measures actual system performance under specific circumstances and is affected by network loads and hardware efficiency.
(Multiple Choice)
4.7/5  (36)
(36)
_____ ensures that authorized users have timely and reliable access to necessary information.
(Multiple Choice)
4.9/5  (31)
(31)
In a broad sense, credentials include formal degrees, diplomas, or certificates granted by learning institutions to show that a certain level of education has been achieved.
(True/False)
4.9/5  (33)
(33)
_____ is a process that monitors current activity and performance levels, anticipates future activity, and forecasts the resources needed to provide desired levels of service.
(Multiple Choice)
4.9/5  (28)
(28)
 -As shown in the accompanying figure, maintenance expenses usually are high when a system is implemented because problems must be detected, investigated, and resolved by _____.
-As shown in the accompanying figure, maintenance expenses usually are high when a system is implemented because problems must be detected, investigated, and resolved by _____.
(Multiple Choice)
4.8/5  (34)
(34)
_____ measures the time between submitting a request for information and the fulfillment of the request.
(Multiple Choice)
4.8/5  (31)
(31)
Many IT departments also use a job title of _____ to designate positions that require a combination of systems analysis and programming skills.
(Multiple Choice)
4.7/5  (27)
(27)
One highly publicized form of social engineering is called post texting, which is a method of obtaining personal information under false pretenses.
(True/False)
4.9/5  (30)
(30)
_____ is concerned with managerial policies and controls that ensure secure operations.
(Multiple Choice)
4.7/5  (33)
(33)
Showing 1 - 20 of 81
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)