Exam 9: Network and Internet Security
Exam 1: Introduction to the World of Computers90 Questions
Exam 2: The System Unit: Processing and Memory91 Questions
Exam 3: Storage90 Questions
Exam 4: Input and Output90 Questions
Exam 5: System Software: Operating Systems and Utility91 Questions
Exam 6: Application Software89 Questions
Exam 7: Computer Networks89 Questions
Exam 8: The Internet and the World Wide Web87 Questions
Exam 9: Network and Internet Security90 Questions
Exam 10: Multimedia and the Web79 Questions
Exam 11: E-Commerce88 Questions
Exam 12: Information Systems and System Development75 Questions
Exam 13: Program Development and Programming Languages73 Questions
Exam 14: Databases and Database Management Systems72 Questions
Exam 15: Computer Security and Privacy88 Questions
Exam 16: Intellectual Property Rights, Ethics, Health, Acccess and the Environment80 Questions
Select questions type
____________________ often find their victims online- for instance, someone in a chat room who makes a comment or has a screen name that they do not like.
(Short Answer)
4.9/5  (30)
(30)
A firewall is a security system that essentially creates a barrier between a computer or network and the Internet in order to protect against unauthorized access.
(True/False)
4.8/5  (35)
(35)
Like a computer virus, a ____ is a malicious program designed to cause damage.
(Multiple Choice)
4.8/5  (39)
(39)
Phishing schemes use legitimate-looking e-mails to trick users into providing private information. _________________________
(True/False)
4.8/5  (43)
(43)
Denial of service attacks are usually of insignificant cost in terms of business lost.
(True/False)
4.8/5  (39)
(39)
____, the most commonly used type of possessed knowledge, are secret words or character combinations associated with an individual.
(Multiple Choice)
4.8/5  (34)
(34)
Digital certificates are obtained from a(n) ____________________ and typically contain the name of the person, organization, or Web site being certified along with a certificate serial number, an expiration date, and a public / private key pair.
(Short Answer)
4.9/5  (41)
(41)
A type of computer infection occurs when a hacker breaches a computer system in order to delete data, change data, modify programs, or otherwise alter the data and programs located there. _________________________
(True/False)
4.9/5  (37)
(37)
A(n) ____________________ is a unique digital code that can be attached to a file or an e-mail message to verify the identity of the sender of a document.
(Short Answer)
4.8/5  (37)
(37)
A(n) denial of service (DoS) attack is an act of sabotage that attempts to flood a network server or Web server with so many requests for action that it cannot handle legitimate requests any longer. _________________________
(True/False)
5.0/5  (38)
(38)
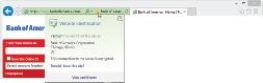 -The green color of the Address bar in the accompanying figure indicates that the site is using a valid ____ SSL certificate.
-The green color of the Address bar in the accompanying figure indicates that the site is using a valid ____ SSL certificate.
(Multiple Choice)
4.8/5  (42)
(42)
When a digitally signed document is received, the recipient's computer uses the sender's ____ key to verify the digital signature.
(Multiple Choice)
4.8/5  (37)
(37)
A ____ is a malicious program that masquerades as something else-usually as some type of application program.
(Multiple Choice)
4.9/5  (33)
(33)
The term ____ refers to accessing someone else's unsecured Wi-Fi network from the hacker's current location (such as inside his or her home, outside a Wi-Fi hotspot location, or near a local business).
(Multiple Choice)
4.8/5  (30)
(30)
A computer that is controlled by a hacker or other computer criminal is referred to as a ____.
(Multiple Choice)
4.9/5  (34)
(34)
____________________ access refers to individuals gaining access to a computer, network, file, or other resource without permission.
(Short Answer)
4.8/5  (24)
(24)
Cuts or other changes to a finger may prevent access via a(n) keystroke reader. _________________________
(True/False)
5.0/5  (44)
(44)
Showing 41 - 60 of 90
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)