Exam 5: Digital Safety and Security: Identifying Threats, Issues, and Defenses
Exam 1: Digital Literacy: Introducing a World of Technology181 Questions
Exam 2: The Internet: Accessing, Searching, Sharing, and Communicating181 Questions
Exam 3: Computers and Mobile Devices: Evaluating the Possibilities181 Questions
Exam 4: Programs and Apps: Using Software at Work, School, and Home181 Questions
Exam 5: Digital Safety and Security: Identifying Threats, Issues, and Defenses181 Questions
Exam 6: Inside Computers and Mobile Devices: Exploring the Components181 Questions
Exam 7: Input and Output: Examining Popular Devices181 Questions
Exam 8: Digital Storage: Preserving on Media and on the Cloud181 Questions
Exam 9: Operating Systems: Managing, Coordinating, and Monitoring Resources181 Questions
Exam 10: Communications and Networks: Sending and Receiving Digital Content181 Questions
Exam 11: Information and Data Management: Organizing, Verifying, Maintaining, and Accessing181 Questions
Exam 12: Information Systems and Program Development: Designing and Building Solutions181 Questions
Select questions type
One way to reduce electrical waste is for organizations to use outside air to cool data centers and computer facilities.
(True/False)
4.9/5  (26)
(26)
In which particularly devastating type of DoS attack are multiple unsuspecting computers used to attack multiple computer networks?
(Multiple Choice)
4.9/5  (43)
(43)
Many organizations and businesses have strict written policies governing the installation and use of software and enforce their rules by checking networked or online computers periodically to ensure that all software is licensed properly.
(True/False)
4.8/5  (31)
(31)
Discuss the seven different categories into which perpetrators of cybercrime and other intrusions fall.
(Not Answered)
This question doesn't have any answer yet
COGNITIVE ASSESSMENT Which of the following refers to a technique intruders use to make their network or Internet transmission appear legitimate to a victim computer or network?
(Multiple Choice)
4.7/5  (33)
(33)
COGNITIVE ASSESSMENT When a waiter at a restaurant steals credit card numbers to make fraudulent purchases, this is called _____________.
(Multiple Choice)
4.9/5  (33)
(33)
COGNITIVE ASSESSMENT Which of the following terms is used to describe a program that copies itself repeatedly, using up resources and possibly shutting down the computer or network?
(Multiple Choice)
4.9/5  (38)
(38)
During virtual browsing, your browser does not keep track of the websites you are visiting.
(True/False)
4.9/5  (31)
(31)
Which kind of license is a legal agreement that permits users to install the software on multiple computers, usually at a volume discount?
(Multiple Choice)
4.7/5  (26)
(26)
COGNITIVE ASSESSMENT Which of the following terms is used to describe a scam in which a website includes a button, image or link that contains a malicious program?
(Multiple Choice)
4.7/5  (32)
(32)
Which of the following is an authorized person or company that issues and verifies digital certificates?
(Multiple Choice)
4.9/5  (39)
(39)
Which of the following refers to unique and original works such as ideas, inventions, writings, art, processes, company and product names, and logos?
(Multiple Choice)
4.9/5  (33)
(33)
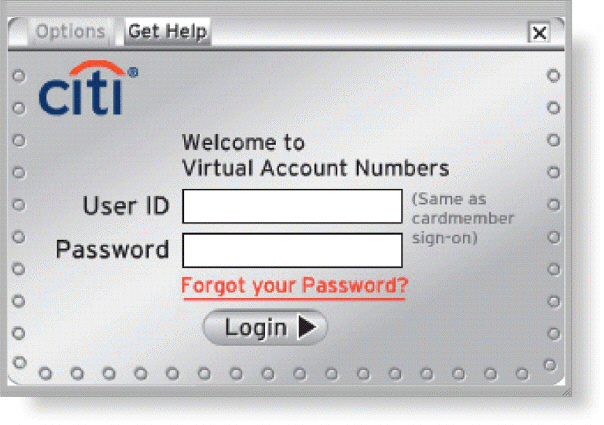 Many websites, like that in the accompanying figure, require a user to enter a private combination of characters associated with a user name that allows access to certain computer resources. What is the term for this combination of characters?
Many websites, like that in the accompanying figure, require a user to enter a private combination of characters associated with a user name that allows access to certain computer resources. What is the term for this combination of characters?
(Multiple Choice)
4.7/5  (42)
(42)
COGNITIVE ASSESSMENT Which of the following does a new federal laboratory use in its high security areas?
(Multiple Choice)
4.9/5  (35)
(35)
Discuss the measures you can take to safeguard home computers and devices.
(Not Answered)
This question doesn't have any answer yet
COGNITIVE ASSESSMENT Which of the following statements is not true about biometric devices?
(Multiple Choice)
4.8/5  (39)
(39)
COGNITIVE ASSESSMENT Which of the following statements is not a safeguard against the failure of hardware?
(Multiple Choice)
4.8/5  (36)
(36)
The Privacy Act forbids federal agencies from allowing information to be used for a reason other than that for which it was collected.
(True/False)
4.8/5  (37)
(37)
Which of the following is a duplicate of a file, program, or disk that can be used if the original is lost, damaged, or destroyed?
(Multiple Choice)
4.8/5  (33)
(33)
Showing 101 - 120 of 181
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)