Exam 5: Digital Safety and Security: Identifying Threats, Issues, and Defenses
Exam 1: Digital Literacy: Introducing a World of Technology181 Questions
Exam 2: The Internet: Accessing, Searching, Sharing, and Communicating181 Questions
Exam 3: Computers and Mobile Devices: Evaluating the Possibilities181 Questions
Exam 4: Programs and Apps: Using Software at Work, School, and Home181 Questions
Exam 5: Digital Safety and Security: Identifying Threats, Issues, and Defenses181 Questions
Exam 6: Inside Computers and Mobile Devices: Exploring the Components181 Questions
Exam 7: Input and Output: Examining Popular Devices181 Questions
Exam 8: Digital Storage: Preserving on Media and on the Cloud181 Questions
Exam 9: Operating Systems: Managing, Coordinating, and Monitoring Resources181 Questions
Exam 10: Communications and Networks: Sending and Receiving Digital Content181 Questions
Exam 11: Information and Data Management: Organizing, Verifying, Maintaining, and Accessing181 Questions
Exam 12: Information Systems and Program Development: Designing and Building Solutions181 Questions
Select questions type
COGNITIVE ASSESSMENT In order to safeguard your personal information, which of the following is recommended?
(Multiple Choice)
4.9/5  (33)
(33)
COGNITIVE ASSESSMENT Which of the following terms is used to describe a file a computer creates that records successful and unsuccessful access attempts?
(Multiple Choice)
4.8/5  (39)
(39)
What is the term for a website that uses encryption techniques to protect its data?
(Multiple Choice)
4.7/5  (36)
(36)
COGNITIVE ASSESSMENT What term is used to describe the discovery, collection, and analysis of evidence found on computers and networks?
(Multiple Choice)
4.9/5  (36)
(36)
An IT code of conduct is a written guideline that helps determine whether a specific computer action is which of the following?
(Multiple Choice)
4.9/5  (35)
(35)
A(n) ____________________ control is a security measure that defines who can access a computer, when they can access it, and what actions they can take while accessing the computer.
(Short Answer)
4.8/5  (35)
(35)
Which encryption algorithm inserts characters between existing characters?
(Multiple Choice)
4.9/5  (31)
(31)
COGNITIVE ASSESSMENT Which of the following does your company use to track your time and attendance?
(Multiple Choice)
4.9/5  (42)
(42)
____________________ is the process of converting readable data into unreadable characters to prevent unauthorized access.
(Short Answer)
4.7/5  (34)
(34)
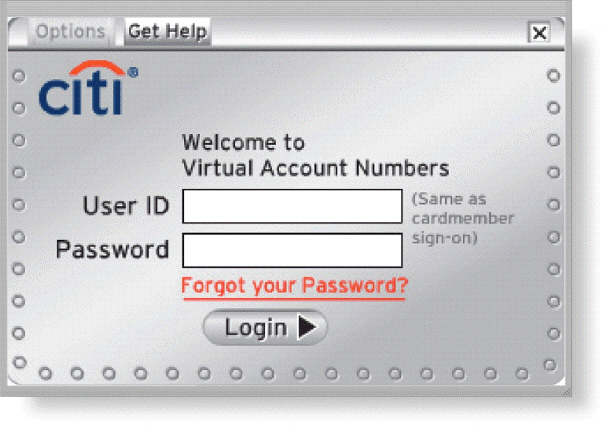 As shown in the accompanying figure, most operating systems require that users correctly enter a user name and password before they can access the data, information, and programs stored on a computer, mobile device, or network.
As shown in the accompanying figure, most operating systems require that users correctly enter a user name and password before they can access the data, information, and programs stored on a computer, mobile device, or network.
(True/False)
4.8/5  (31)
(31)
COGNITIVE ASSESSMENT The term, payload, as it pertains to computer crime, is defined as _____________.
(Multiple Choice)
4.7/5  (34)
(34)
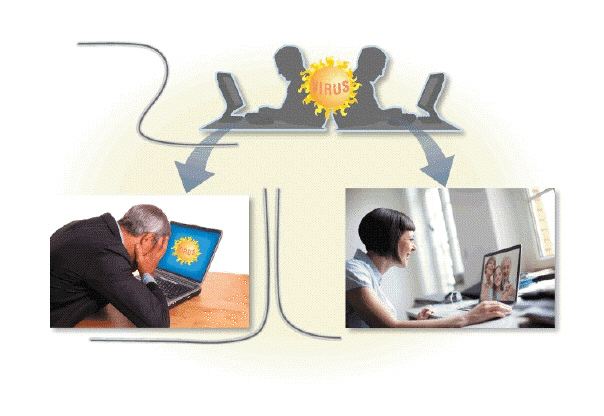 Computer viruses like the kind in the accompanying figure-along with worms, and Trojan horses-deliver their ____________________ on a computer or mobile device when a user opens an infected file or runs an infected program.
Computer viruses like the kind in the accompanying figure-along with worms, and Trojan horses-deliver their ____________________ on a computer or mobile device when a user opens an infected file or runs an infected program.
(Short Answer)
4.7/5  (25)
(25)
 A(n) ____________________ is a wireless network name, which you should change from the default to something that uniquely identifies your network, like the kind in the accompanying figure, especially if you live in close proximity to other wireless networks.
A(n) ____________________ is a wireless network name, which you should change from the default to something that uniquely identifies your network, like the kind in the accompanying figure, especially if you live in close proximity to other wireless networks.
(Short Answer)
4.8/5  (30)
(30)
One way to reduce electrical waste is for organizations to consolidate servers by user concatenation.
(True/False)
5.0/5  (41)
(41)
COGNITIVE ASSESSMENT Which of the following best describes the term, cybercrime?
(Multiple Choice)
4.8/5  (33)
(33)
COGNITIVE ASSESSMENT What is the general term for programs that act without a user's knowledge and deliberately alter the computer's operations?
(Multiple Choice)
4.8/5  (33)
(33)
COGNITIVE ASSESSMENT You have just provided the identification number that associates your new software purchase with the mobile device on which you installed the software. What is the term for this process?
(Multiple Choice)
4.8/5  (36)
(36)
Showing 161 - 180 of 181
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)