Exam 9: Network and Internet Security
Exam 1: Introduction to the World of Computers100 Questions
Exam 2: The System Unit: Processing and Memory100 Questions
Exam 3: Storage100 Questions
Exam 4: Input and Output100 Questions
Exam 5: System Software: Operating Systems and Utility Programs100 Questions
Exam 6: Application Software100 Questions
Exam 7: Computer Networks100 Questions
Exam 8: The Internet and the World Wide Web100 Questions
Exam 9: Network and Internet Security100 Questions
Select questions type
Botnets are a major security threat since criminals are increasingly creating botnets to use for computer sabotage.
Free
(True/False)
5.0/5  (41)
(41)
Correct Answer:
True
Unauthorized use involves using a computer resource for unauthorized activities.
Free
(True/False)
4.8/5  (29)
(29)
Correct Answer:
True
In businesses, access control systems are often integrated into a comprehensive ____________________ system designed to manage users' access to enterprise systems.
Free
(Short Answer)
4.7/5  (40)
(40)
Correct Answer:
IDM
A(n) denial of service (DoS) attack is an act of sabotage that attempts to flood a network server or Web server with so many requests for action that it cannot handle legitimate requests any longer.
(True/False)
5.0/5  (37)
(37)
Identification systems determine whether or not the person attempting access is actually who he or she claims to be.
(True/False)
4.9/5  (42)
(42)
A(n) ____________________ is a unique digital code that can be attached to a file or an e-mail message to verify the identity of the sender of a document.
(Short Answer)
4.9/5  (37)
(37)
A ____ provides a secure private tunnel from the user's computer through the Internet to another destination and is most often used to provide remote employees with secure access to a company network.
(Multiple Choice)
4.8/5  (42)
(42)
Like a computer virus, a ____ is a malicious program designed to cause damage.
(Multiple Choice)
4.8/5  (41)
(41)
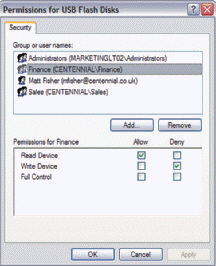 ____ software, such as that shown in the accompanying figure, can control which devices can be connected to an employee's computer.
____ software, such as that shown in the accompanying figure, can control which devices can be connected to an employee's computer.
(Multiple Choice)
4.8/5  (42)
(42)
AntiDoS software is used to detect and eliminate computer viruses and other types of malware.
(True/False)
4.9/5  (31)
(31)
____ uses a single secret key to both encrypt and decrypt the file or message.
(Multiple Choice)
4.8/5  (30)
(30)
A computer ____ is a software program that is installed without the permission or knowledge of the computer user, that is designed to alter the way a computer operates, and that can replicate itself to infect any new media it has access to.
(Multiple Choice)
4.9/5  (35)
(35)
The purpose of a(n) ____________________ is to authenticate the identity of an individual or organization.
(Short Answer)
4.9/5  (33)
(33)
A ____ is a malicious program that masquerades as something else-usually as some type of application program.
(Multiple Choice)
5.0/5  (35)
(35)
A computer that is controlled by a hacker or other computer criminal is referred to as a ____.
(Multiple Choice)
4.9/5  (40)
(40)
Showing 1 - 20 of 100
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)