Exam 9: Network and Internet Security
Exam 1: Introduction to the World of Computers100 Questions
Exam 2: The System Unit: Processing and Memory100 Questions
Exam 3: Storage100 Questions
Exam 4: Input and Output100 Questions
Exam 5: System Software: Operating Systems and Utility Programs100 Questions
Exam 6: Application Software100 Questions
Exam 7: Computer Networks100 Questions
Exam 8: The Internet and the World Wide Web100 Questions
Exam 9: Network and Internet Security100 Questions
Select questions type
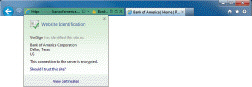 The green color of the Address bar in the accompanying figure indicates that the site is using a valid ____ SSL certificate.
The green color of the Address bar in the accompanying figure indicates that the site is using a valid ____ SSL certificate.
(Multiple Choice)
4.8/5  (29)
(29)
Possessed knowledge access systems use physical objects for identification purposes and are frequently used to access facilities and computer systems.
(True/False)
4.9/5  (46)
(46)
Antispam programs are used to detect and remove any viruses or worms that find their way onto your computer.
(True/False)
5.0/5  (38)
(38)
Case-Based Critical Thinking Questions Case 9-1 Melissa is the network administrator for a small publishing company. As network administrator, she is in charge of maintaining the security of all the computers that are part of the company's network. One of the first items that Melissa installed was a(n) ____, which checks all incoming and outgoing traffic and only allows authorized traffic to pass through.
(Multiple Choice)
4.8/5  (42)
(42)
The ____, implemented in 2001, grants federal authorities expanded surveillance and intelligence-gathering powers, such as broadening their ability to obtain the real identity of Internet users and to intercept Internet communications.
(Multiple Choice)
4.8/5  (36)
(36)
One emerging type of Trojan horse is called a ____-Access Trojan.
(Multiple Choice)
4.9/5  (39)
(39)
Public key encryption is also called ____________________ encryption.
(Short Answer)
4.9/5  (39)
(39)
____ access systems use physical objects for identification purposes and they are frequently used to control access to facilities and computer systems.
(Multiple Choice)
4.9/5  (40)
(40)
____ occurs whenever an individual gains access to a computer, network, file, or other resource without permission.
(Multiple Choice)
4.8/5  (36)
(36)
It is important to select strong passwords and change them frequently.
(True/False)
4.7/5  (37)
(37)
A group of bots that are controlled by one individual and can work together in a coordinated fashion is called a(n) ____________________.
(Short Answer)
4.8/5  (47)
(47)
Antivirus programs are usually set up to automatically download new ____ from their associated Web site on a regular basis.
(Multiple Choice)
4.9/5  (46)
(46)
____ identify users by a particular unique biological characteristic.
(Multiple Choice)
4.8/5  (39)
(39)
Digital certificates are obtained from a(n) ____________________ and typically contain the name of the person, organization, or Web site being certified along with a certificate serial number, an expiration date, and a public/private key pair.
(Short Answer)
5.0/5  (47)
(47)
Biometric authentication uses information that an individual should know or can easily remember.
(True/False)
4.8/5  (40)
(40)
____ are sets of tools that allow hackers to access a system.
(Multiple Choice)
5.0/5  (37)
(37)
A(n) ____________________ access system is an identification system that requires the individual requesting access to provide information that only the authorized user is supposed to know.
(Short Answer)
4.9/5  (44)
(44)
Typically, ____________________ begins with obtaining a person's name and Social Security number, often from a credit application, rental application, or similar form.
(Short Answer)
4.8/5  (33)
(33)
Some Web-based encrypted e-mail systems-such as the popular free ____ service-require both the sender and recipient to have accounts through that system.
(Multiple Choice)
4.8/5  (35)
(35)
Once installed, ____________________ are designed to record every keystroke made on the infected computer and transmit account numbers, passwords, and other related information to criminals.
(Short Answer)
4.8/5  (30)
(30)
Showing 41 - 60 of 100
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)