Exam 6: Digital Safety and Security: Identifying Threats, Issues, and Defenses
Exam 1: Office 2013 and Windows 8 Essential Concepts and Skills112 Questions
Exam 2: Digital Literacy: Introducing a World of Technology200 Questions
Exam 3: The Internet: Accessing, Searching, Sharing, and Communicating200 Questions
Exam 4: Computers and Mobile Devices: Evaluating the Possibilities200 Questions
Exam 5: Programs and Apps: Using Software at Work, School, and Home200 Questions
Exam 6: Digital Safety and Security: Identifying Threats, Issues, and Defenses200 Questions
Exam 7: Access: Databases and Database Objects: an Introduction112 Questions
Exam 8: Access: Querying a Database112 Questions
Exam 9: Excel: Creating a Worksheet and a Chart112 Questions
Exam 10: Excel: Formulas, Functions, and Formatting112 Questions
Exam 11: Excel: Working With Large Worksheets, Charting, and What-If Analysis111 Questions
Exam 12: Powerpoint: Creating and Editing a Presentation With Pictures112 Questions
Exam 13: Powerpoint: Enhancing a Presentation With Pictures, Shapes, and Wordart112 Questions
Exam 14: Powerpoint: Reusing a Presentation and Adding Media and Animation112 Questions
Exam 15: Word: Creating, Formatting, and Editing a Word Document With a Picture112 Questions
Exam 16: Word: Creating a Research Paper With References and Sources112 Questions
Exam 17: Word: Creating a Business Letter With a Letterhead and Table112 Questions
Select questions type
COGNITIVE ASSESSMENT The term, botnet, means _____________.
(Multiple Choice)
4.7/5  (44)
(44)
Which kind of license is a legal agreement that permits users to install the software on multiple computers, usually at a volume discount?
(Multiple Choice)
4.8/5  (31)
(31)
Which of the following is someone who uses the Internet or network to destroy or damage computers for political reasons?
(Multiple Choice)
4.9/5  (40)
(40)
COGNITIVE ASSESSMENT Which of the following does your college use to verify your identity?
(Multiple Choice)
4.8/5  (39)
(39)
Both Windows and Mac operating systems include firewall capabilities.
(True/False)
4.7/5  (36)
(36)
COGNITIVE ASSESSMENT Which of the following is the least likely motive for a DDoS?
(Multiple Choice)
4.9/5  (38)
(38)
Discuss a virus and related examples of malware, also include definitions of the term payload, and a discussion of how a virus delivers a payload in your answer.Explain a common way through which computers and mobile devices become infected with viruses, and list common types of malware
(Essay)
4.8/5  (38)
(38)
Which of the following laws provides the same protection that covers mail and telephone communications to electronic communications such as voice mail?
(Multiple Choice)
4.9/5  (39)
(39)
Which law states that it is not illegal to intercept or access an electronic communication made through an electronic communication system that is configured so that such electronic communication is readily accessible to the general public?
(Multiple Choice)
4.9/5  (37)
(37)
COGNITIVE ASSESSMENT The term back door, as it refers to computer crime, is _____________.
(Multiple Choice)
4.8/5  (40)
(40)
Which of the following is a federally funded Internet security research and development center?
(Multiple Choice)
4.8/5  (47)
(47)
Internet advertising firms often use which of the following to collect information about users web browsing habits?
(Multiple Choice)
4.9/5  (40)
(40)
Which of the following is a technique intruders use to make their network or Internet transmission appear legitimate to a victim computer or network?
(Multiple Choice)
4.9/5  (41)
(41)
Personal computers, display devices, and printers should comply with guidelines of which of the following programs?
(Multiple Choice)
4.8/5  (49)
(49)
Cybercrime laws are consistent between states and countries, making it easy to reach a consensus as to what is illegal.
(True/False)
4.9/5  (45)
(45)
Proximity sharing gives websites access to your current location.
(True/False)
4.9/5  (33)
(33)
Websites use which of the following to keep track of items in a user's shopping cart?
(Multiple Choice)
4.9/5  (38)
(38)
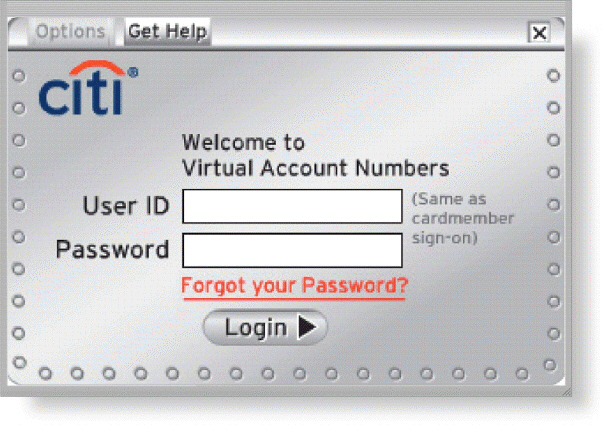 Many websites, like that in the accompanying figure, require a user to enter a private combination of characters associated with a user name that allows access to certain computer resources.What is the term for this combination of characters?
Many websites, like that in the accompanying figure, require a user to enter a private combination of characters associated with a user name that allows access to certain computer resources.What is the term for this combination of characters?
(Multiple Choice)
4.9/5  (36)
(36)
Showing 121 - 140 of 200
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)