Exam 6: Data Security
Exam 1: Computer and Internet Basics91 Questions
Exam 2: Computer Hardware91 Questions
Exam 3: Computer Software91 Questions
Exam 4: Digital Electronics and File Management91 Questions
Exam 5: Networks and the Internet93 Questions
Exam 6: Data Security91 Questions
Exam 7: The Web and E-Commerce91 Questions
Exam 8: Digital Media91 Questions
Exam 9: The Computer Industry and Careers91 Questions
Exam 10: Trends in Technology61 Questions
Select questions type
____ is the term used to describe terrorist acts committed via the Internet.
Free
(Multiple Choice)
5.0/5  (34)
(34)
Correct Answer:
B
 Which of the following statements it NOT true about the figure shown above?
Which of the following statements it NOT true about the figure shown above?
Free
(Multiple Choice)
4.9/5  (40)
(40)
Correct Answer:
D
When storing your backup files on a LAN, consider each of the following EXCEPT ____:
Free
(Multiple Choice)
4.8/5  (35)
(35)
Correct Answer:
D
MTBF is a rating that attempts to measure the time before a(n)____ failure occurs.
(Multiple Choice)
4.7/5  (33)
(33)
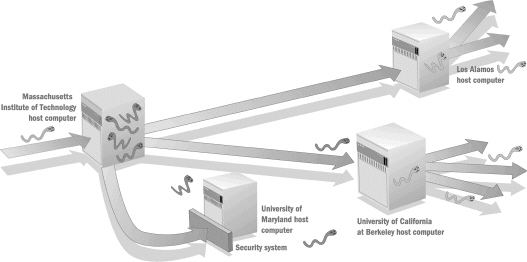 In the figure above, the worm enters the original host and other unprotected hosts using ____.
In the figure above, the worm enters the original host and other unprotected hosts using ____.
(Multiple Choice)
4.8/5  (35)
(35)
 The device shown in the figure above provides the best protection against power problems. What is the name for this device?
The device shown in the figure above provides the best protection against power problems. What is the name for this device?
(Multiple Choice)
4.9/5  (23)
(23)
Which of the following is NOT an appliance designed to protect electrical devices from power surges and voltage spikes?
(Multiple Choice)
4.8/5  (29)
(29)
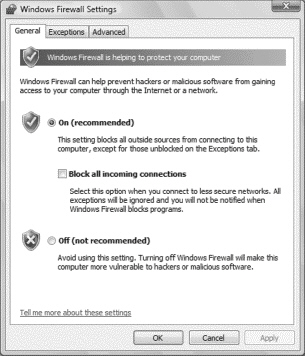 Windows Vista includes firewall software, as shown above, and can be configured from the Support Center.
Windows Vista includes firewall software, as shown above, and can be configured from the Support Center.
(True/False)
4.8/5  (33)
(33)
The Windows ____ is a file that stores configuration information about the devices and software installed on a computer system.
(Multiple Choice)
4.7/5  (40)
(40)
A ____ is a program that seems to perform one function, while actually doing something else.
(Multiple Choice)
4.9/5  (34)
(34)
 The power strip shown in the figure above is an appliance designed to protect electrical devices from power surges and voltage spikes.
The power strip shown in the figure above is an appliance designed to protect electrical devices from power surges and voltage spikes.
(True/False)
4.9/5  (34)
(34)
A(n)____ backup contains a copy of every program, data, and system file on a computer.
(Multiple Choice)
4.9/5  (33)
(33)
____ is a type of program that secretly gathers personal information without the victim's knowledge, usually for advertising and other commercial purposes.
(Multiple Choice)
4.9/5  (38)
(38)
A ____ is a person who controls many bot-infested computers.
(Multiple Choice)
4.9/5  (38)
(38)
A facility that is designed to house and protect a computer system and its data is called a(n)____ center.
(Multiple Choice)
4.9/5  (38)
(38)
List three ways to prevent your computer from becoming infected by malware.
(Essay)
4.9/5  (29)
(29)
A password ____________________ is utility software that generates secure passwords and stores them along with user IDs.
(Short Answer)
4.8/5  (34)
(34)
Biometrics is a method of authentication used to confirm a person's identity based on some physical trait.
(True/False)
4.8/5  (36)
(36)
Showing 1 - 20 of 91
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)