Exam 6: Data Security
Exam 1: Computer and Internet Basics91 Questions
Exam 2: Computer Hardware91 Questions
Exam 3: Computer Software91 Questions
Exam 4: Digital Electronics and File Management91 Questions
Exam 5: Networks and the Internet93 Questions
Exam 6: Data Security91 Questions
Exam 7: The Web and E-Commerce91 Questions
Exam 8: Digital Media91 Questions
Exam 9: The Computer Industry and Careers91 Questions
Exam 10: Trends in Technology61 Questions
Select questions type
Human error, also called ____________________ error, includes entering inaccurate data or not following procedures.
(Short Answer)
4.9/5  (34)
(34)
Backup software is a set of ____ programs designed to back up and restore files.
(Multiple Choice)
4.7/5  (27)
(27)
A ____ usually arrives as an email message containing warnings of a new virus.
(Multiple Choice)
4.8/5  (43)
(43)
When referring to war driving and war chalking, war stands for ____.
(Multiple Choice)
4.8/5  (39)
(39)
Encryption transforms a message so that its contents are hidden from unauthorized readers.
(True/False)
4.8/5  (34)
(34)
Viruses programmed to deliver their payloads on a certain date are called time bombs.
(True/False)
4.8/5  (29)
(29)
A virus ____ is a file that your antivirus software uses to identify and remove malware.
(Multiple Choice)
4.9/5  (39)
(39)
Your coworker, Casey, asks you to explain the differences in a password and a PIN. What would you tell her?
(Essay)
4.9/5  (37)
(37)
Authentication protocols that use more than one means of identification are ____ secure than others.
(Multiple Choice)
4.7/5  (47)
(47)
A(n)____ verifies a user ID and guarantees that you are the person you claim to be.
(Multiple Choice)
4.9/5  (42)
(42)
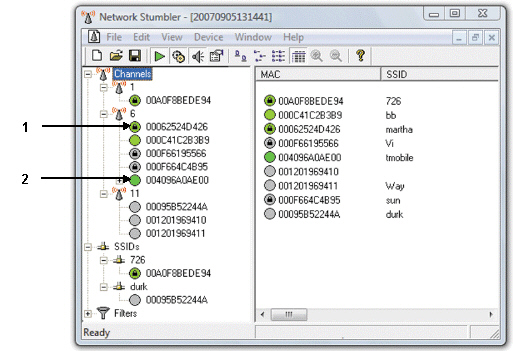 LANjackers use network-detecting and monitoring software, like the software shown in the figure above, to help locate and identify secured and unsecured networks.
LANjackers use network-detecting and monitoring software, like the software shown in the figure above, to help locate and identify secured and unsecured networks.
(True/False)
4.8/5  (32)
(32)
____ scrambles the data transmitted between wireless devices and then unscrambles the data only on devices that have a valid key.
(Multiple Choice)
4.9/5  (40)
(40)
____________________ authentication verifies identity using two independent elements of confirmation.
(Short Answer)
4.8/5  (37)
(37)
Describe at least five tips for keeping your computer system in good working condition.
(Essay)
4.8/5  (35)
(35)
____________________ protocol refers to any method that confirms a person's identity when using a computer system.
(Short Answer)
4.8/5  (34)
(34)
You have just been hired as an assistant to the network administrator at a local company. You are asked to give a presentation on viruses, worms, bots, Trojans, and spyware and include the unauthorized activities the network might see if malware enters the company's network. The servers on the network are flooded with useless traffic. The servers' processing capabilities are overwhelmed, and all communications have been stopped. What is probably happening?
(Essay)
4.8/5  (32)
(32)
A(n)____________________ is your unique identifier on a computer or Web page.
(Short Answer)
4.8/5  (41)
(41)
Showing 21 - 40 of 91
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)