Exam 6: Data Security
Exam 1: Computer and Internet Basics91 Questions
Exam 2: Computer Hardware91 Questions
Exam 3: Computer Software91 Questions
Exam 4: Digital Electronics and File Management91 Questions
Exam 5: Networks and the Internet93 Questions
Exam 6: Data Security91 Questions
Exam 7: The Web and E-Commerce91 Questions
Exam 8: Digital Media91 Questions
Exam 9: The Computer Industry and Careers91 Questions
Exam 10: Trends in Technology61 Questions
Select questions type
Which of the following is NOT an objective of risk management?
(Multiple Choice)
4.9/5  (29)
(29)
A(n)____________________ attack helps hackers guess your password by stepping through a list of thousands of the most common passwords.
(Short Answer)
5.0/5  (41)
(41)
 Publications like the one shown above help risk management professionals design and update disaster recovery plans.
Publications like the one shown above help risk management professionals design and update disaster recovery plans.
(True/False)
4.8/5  (39)
(39)
____ involves writing specific symbols on walls, sidewalks, or lampposts to signal others they can tap into a wireless network in the area.
(Multiple Choice)
4.9/5  (29)
(29)
You have just been hired as an assistant to the network administrator at a local company. You are asked to give a presentation on viruses, worms, bots, Trojans, and spyware and include the unauthorized activities the network might see if malware enters the company's network. A coworker contacts you to inspect the computer in her office. She suspects that it is infected with malware. What steps will you take?
(Essay)
4.7/5  (16)
(16)
A(n)virus ____ is a section of program code that can be used to identify a known malicious program.
(Multiple Choice)
4.7/5  (35)
(35)
You do not have to click anything to receive a third-party cookie generated by a ____.
(Multiple Choice)
4.8/5  (38)
(38)
A boot disk contains a complete copy of your computer's hard disk as it existed when shipped from the manufacturer.
(True/False)
4.9/5  (34)
(34)
Worms attach themselves to a file, reproduce, and spread to other files on the same computer.
(True/False)
4.8/5  (40)
(40)
A firewall is software or hardware designed to filter out suspicious packets attempting to enter or leave a computer.
(True/False)
4.8/5  (35)
(35)
 Which of the following statements it NOT true about the figure shown above?
Which of the following statements it NOT true about the figure shown above?
(Multiple Choice)
4.8/5  (32)
(32)
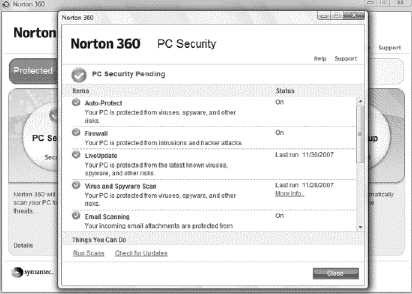 A security suite , which integrates several security modules, is shown in the figure above.
A security suite , which integrates several security modules, is shown in the figure above.
(True/False)
4.8/5  (36)
(36)
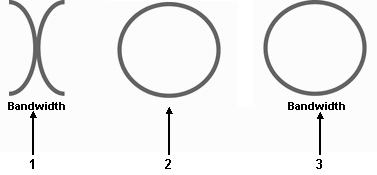 Item ____ in the figure above indicates an open (available)node.
Item ____ in the figure above indicates an open (available)node.
(Multiple Choice)
4.8/5  (37)
(37)
Showing 61 - 80 of 91
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)