Exam 7: Procedures for Responding to Attacks on Computers
Exam 1: Introduction to Disaster Recovery56 Questions
Exam 2: Preparing to Develop the Disaster Recovery Plan53 Questions
Exam 3: Assessing Risks in the Enterprise63 Questions
Exam 4: Prioritizing Systems and Functions for Recovery60 Questions
Exam 5: Developing Plans and Procedures63 Questions
Exam 6: Organizational Relationships in Disaster Recovery55 Questions
Exam 7: Procedures for Responding to Attacks on Computers65 Questions
Exam 8: Developing Procedures for Special Circumstances58 Questions
Exam 9: Implementing Disaster Recovery Plans65 Questions
Exam 10: Testing and Rehearsal57 Questions
Exam 11: Continued Assessment of Needs Threats and Solutions60 Questions
Exam 12: Living Through a Disaster58 Questions
Select questions type
What type of negative economic impact from computer attacks might include reduced market valuation, stock prices, investor confidence, and goodwill toward the organization?
Free
(Multiple Choice)
4.7/5  (33)
(33)
Correct Answer:
D
Which of the following are all important parts of comprehensive IT security policies and procedures?
Free
(Multiple Choice)
4.8/5  (37)
(37)
Correct Answer:
D
Until recently, the Organization for Cooperation and Development has been at the forefront of addressing privacy issues .
Free
(True/False)
4.9/5  (37)
(37)
Correct Answer:
True
The ____ Web site provides information that can serve as an introduction to disaster recovery planning.
(Multiple Choice)
4.9/5  (35)
(35)
What type of threat could originate from any employee who has physical access to equipment and legitimate rights to information within the organization?
(Multiple Choice)
4.9/5  (33)
(33)
What type of negative economic impact from computer attacks might include damage to systems, the direct costs of repairing or replacing systems, and disrupted business and revenues?
(Multiple Choice)
4.8/5  (33)
(33)
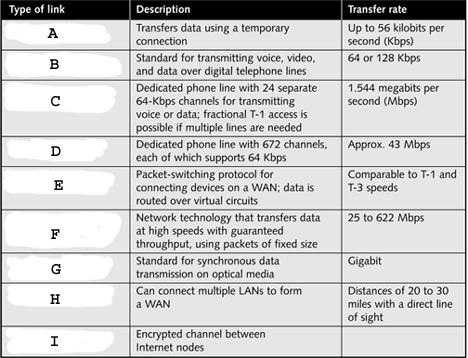 " style="vertical-align: 0px;" width="468px" height="358px In the table above, what does E represent?
" style="vertical-align: 0px;" width="468px" height="358px In the table above, what does E represent?
(Multiple Choice)
4.8/5  (29)
(29)
One popular model for categorizing threats separates information warfare into three categories. What are they?
(Essay)
4.9/5  (32)
(32)
The ____ Web site provides information on the cost of downtime.
(Multiple Choice)
4.9/5  (37)
(37)
An internal threat would originate from any employee who has physical access to equipment and legitimate rights to information within the organization.
(True/False)
4.8/5  (20)
(20)
____ attacks can occur when a hacker has access to packets that come across a network.
(Multiple Choice)
4.8/5  (30)
(30)
____ are a type of trust exploitation attack that uses a compromised host to pass traffic through a firewall that would otherwise be dropped.
(Multiple Choice)
4.9/5  (32)
(32)
In the information warfare model, which of the following is a classification of victim?
(Multiple Choice)
4.8/5  (30)
(30)
____ attacks can occur during the client-server "handshake", a sequence of messages required when a client attempts to establish a TCP connection to a server.
(Multiple Choice)
4.9/5  (44)
(44)
____ attacks occur when a hacker inside or outside a network pretends to be a trusted computer.
(Multiple Choice)
4.9/5  (38)
(38)
The national InfraGard program provides what 4 basic services to members?
(Essay)
4.9/5  (32)
(32)
The explosive growth of networks and Internet connections gives attackers almost limitless opportunities to probe until they find a network with a security flaw they can exploit.
(True/False)
4.8/5  (33)
(33)
With ____ attacks, an intruder takes control of many systems to launch an attack.
(Multiple Choice)
4.8/5  (42)
(42)
The adverse impact of a hacking attack or intrusion can also be described in terms of what three types of losses?
(Essay)
4.8/5  (34)
(34)
The ____ Web site provides data on the hidden cost of downtime from a variety of articles, research reports, and consulting firms.
(Multiple Choice)
5.0/5  (33)
(33)
Showing 1 - 20 of 65
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)