Exam 7: Procedures for Responding to Attacks on Computers
Exam 1: Introduction to Disaster Recovery56 Questions
Exam 2: Preparing to Develop the Disaster Recovery Plan53 Questions
Exam 3: Assessing Risks in the Enterprise63 Questions
Exam 4: Prioritizing Systems and Functions for Recovery60 Questions
Exam 5: Developing Plans and Procedures63 Questions
Exam 6: Organizational Relationships in Disaster Recovery55 Questions
Exam 7: Procedures for Responding to Attacks on Computers65 Questions
Exam 8: Developing Procedures for Special Circumstances58 Questions
Exam 9: Implementing Disaster Recovery Plans65 Questions
Exam 10: Testing and Rehearsal57 Questions
Exam 11: Continued Assessment of Needs Threats and Solutions60 Questions
Exam 12: Living Through a Disaster58 Questions
Select questions type
When people or groups use computer technology, software, and networks to attack systems, they launch a malicious code attack .
(True/False)
4.9/5  (30)
(30)
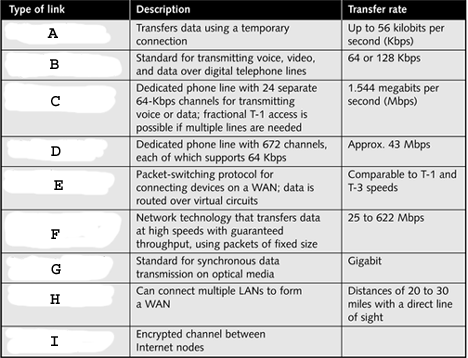 " style="vertical-align: 0px;" width="468px" height="358px In the table above, what does H represent?
" style="vertical-align: 0px;" width="468px" height="358px In the table above, what does H represent?
(Multiple Choice)
4.8/5  (35)
(35)
The CERT Coordination Center provides professional information and security awareness services to defense contractors, governments, and industrial security executives.
(True/False)
4.9/5  (36)
(36)
Most organizations have insurance that covers damage produced by major privacy violations.
(True/False)
4.8/5  (39)
(39)
____ combines features of several DoS attacks, including TFN.
(Multiple Choice)
4.8/5  (41)
(41)
Securing systems against direct or indirect attack requires dividing internal and external threats into cohesive and manageable elements early in the business analysis.
(True/False)
4.8/5  (37)
(37)
What should organizations consider when developing procedures to deal with information warfare threats and damages? (List all 5)
(Essay)
4.7/5  (36)
(36)
The National Strategy for the Physical Protection of Critical Infrastructures and Key Assets document calls for cooperation among government, industry ,and private citizens to protect which key assets? (List 5)
(Essay)
4.7/5  (30)
(30)
How many FBI field offices have established an InfraGard chapter?
(Multiple Choice)
4.9/5  (30)
(30)
What type of negative economic impact from computer attacks might include lost contracts, sales, or customers, a tarnished reputation, and problems in developing new business?
(Multiple Choice)
4.7/5  (34)
(34)
Which legislation requires financial institutions to disclose their privacy policies to customers?
(Multiple Choice)
4.8/5  (35)
(35)
____ attacks refer to malicious software that is attached to another program to execute an unwanted function on a user workstation.
(Multiple Choice)
4.9/5  (32)
(32)
Which legislation limits the use and disclosure of customer proprietary network information (CPNI)by telecommunications service providers?
(Multiple Choice)
4.8/5  (32)
(32)
Threats, such as industrial espionage or a malicious act toward a senior staff member, are deliberate .
(True/False)
5.0/5  (37)
(37)
The most expensive code attack was the Code Red virus at $8.75 billion.
(True/False)
4.9/5  (37)
(37)
List and describe the negative economic effects an organization could endure as a result of computer attacks or intrusions.
(Essay)
4.7/5  (37)
(37)
Securing a system against intrusion is an immense and difficult task.
(True/False)
4.8/5  (40)
(40)
Which act authorizes sharing of the federal government information-gathering efforts with relevant foreign, state, and local officials?
(Multiple Choice)
4.8/5  (27)
(27)
Showing 21 - 40 of 65
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)