Exam 7: The Web and E-Mail
Exam 1: Computers and Digital Basics170 Questions
Exam 2: Computer Hardware175 Questions
Exam 3: Computer Software175 Questions
Exam 4: Operating Systems and File Management175 Questions
Exam 5: Lans and Wlans175 Questions
Exam 6: The Internet175 Questions
Exam 7: The Web and E-Mail175 Questions
Exam 8: Digital Media175 Questions
Exam 9: The Computer Industry: History, Careers, and Ethics175 Questions
Exam 10: Information Systems Analysis and Design175 Questions
Exam 11: Databases175 Questions
Exam 12: Computer Programming175 Questions
Select questions type
A(n) ____________________ is an advertisement, typically embedded at the top of a Web page.
(Short Answer)
4.8/5  (46)
(46)
The major advantage of POP e-mail is that you can access your messages from any computer connected to the Internet.
(True/False)
4.8/5  (40)
(40)
Web-based mail allows you to use a(n) ____ as e-mail client software.
(Multiple Choice)
4.9/5  (33)
(33)
Pharming is less surreptitious and easier to detect than most other hacker schemes.
(True/False)
4.7/5  (35)
(35)
HTML documents use special instructions, called HTML logos , that specify how the document should appear when displayed on a computer screen or printed.
(True/False)
4.9/5  (36)
(36)
When your browser fetches pages and graphics to form a Web page, it stores that material on your computer in temporary files sometimes referred to as a Web ____.
(Multiple Choice)
4.8/5  (29)
(29)
Online auctions and rummage sales are examples of C2C e-commerce.
(True/False)
4.8/5  (43)
(43)
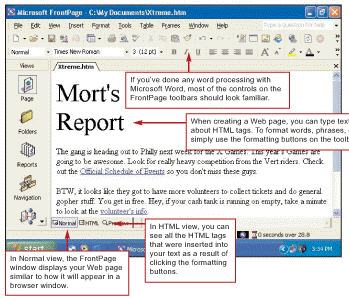 ____, as shown in the above figure, provides tools specifically designed to enter and format Web page text, graphics, and links.
____, as shown in the above figure, provides tools specifically designed to enter and format Web page text, graphics, and links.
(Multiple Choice)
4.9/5  (30)
(30)
A(n) ____ ad overlays the content on a Web page, sometimes obscuring it until you click the ad or its timer expires and the ad disappears.
(Multiple Choice)
4.8/5  (38)
(38)
A(n) Web browser is a software program that runs on your computer and helps you access Web pages.
(True/False)
4.9/5  (23)
(23)
In banking jargon, a one-time-use credit card number is called a controlled payment number.
(True/False)
4.9/5  (43)
(43)
____________________ is an exploit that redirects users to fake sites by "poisoning" a domain name server with a false IP address.
(Short Answer)
4.8/5  (39)
(39)
Three types of e-mail systems are widely used today: SMTP , POP, and Web-based mail.
(True/False)
4.7/5  (33)
(33)
A(n) ____________________ is a cyberspace version of the metal cart you wheel around a store and fill up with merchandise.
(Short Answer)
4.8/5  (32)
(32)
____________________ is an extension of HTTP that simply encrypts the text of an HTTP message before it is sent.
(Short Answer)
4.9/5  (36)
(36)
Showing 41 - 60 of 175
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)